In this Sherlock lab, you will familiarize yourself with Sysmon logs and various useful EventIDs for identifying and analyzing malicious activities on a Windows system. Palo Alto’s Unit42 recently conducted research on an UltraVNC campaign, wherein attackers utilized a backdoored version of UltraVNC to maintain access to systems. This lab is inspired by that campaign and guides participants through the initial access stage of the campaign.
Understanding the Scenario
The UltraVNC campaign, recently researched by Palo Alto’s Unit42, involved attackers using a backdoored version of the legitimate remote access tool, UltraVNC. This allowed them to maintain unauthorized access to compromised systems. The significance of this campaign lies in its stealthy approach, leveraging trusted software to evade detection and gain persistence on targeted systems. Understanding this campaign helps cybersecurity professionals recognize the importance of monitoring for unexpected behaviors in commonly used applications.
Setting Up the Environment
To get started with accessing our forensic files provided by hack the box we will download the ZIP file and remember the password used to open it
Personally I am going to import them into my digital forensic VM that I have set up and work on them there but you can work on them from your personal machine or go over my DFIR workstation guide and create your own
Tools Needed
After downloading and opening the zip file using the password provided on our forensic VM we are greeted with one file
Windows sysmon logs
Sysmon (System Monitor) is a powerful Windows system service and device driver that logs system activity to the Windows event log. By capturing detailed information about process creations, network connections, and file changes, Sysmon provides crucial insights into the behavior of a system. This makes it an invaluable tool for detecting and investigating malicious activities. Utilizing Sysmon logs, security analysts can trace the actions of malware, identify anomalies, and respond swiftly to potential threats, enhancing the overall security posture of an organization.
to view our sysmon logs you can use the standard windows event viewer, but I prefer to use the event explorer which can be found here https://eventlogxp.com/
Event Log Explorer (ELEX)
I prefer ELEX to the standard windows event log due to its advanced search features and ease of use. it also comes with a free personal license so you don’t have to worry about having to pay for it
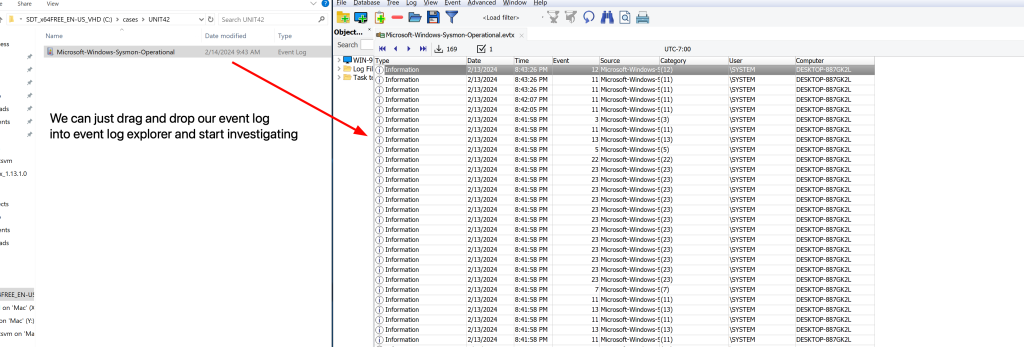
Exploring Sysmon Logs
Our first question is related to the amount of sysmon ID 11’s that show up in our event log to find this you would click on the filter tool in the tool bar and then use the event ID 11 to filter for events that contain that sysmon ID
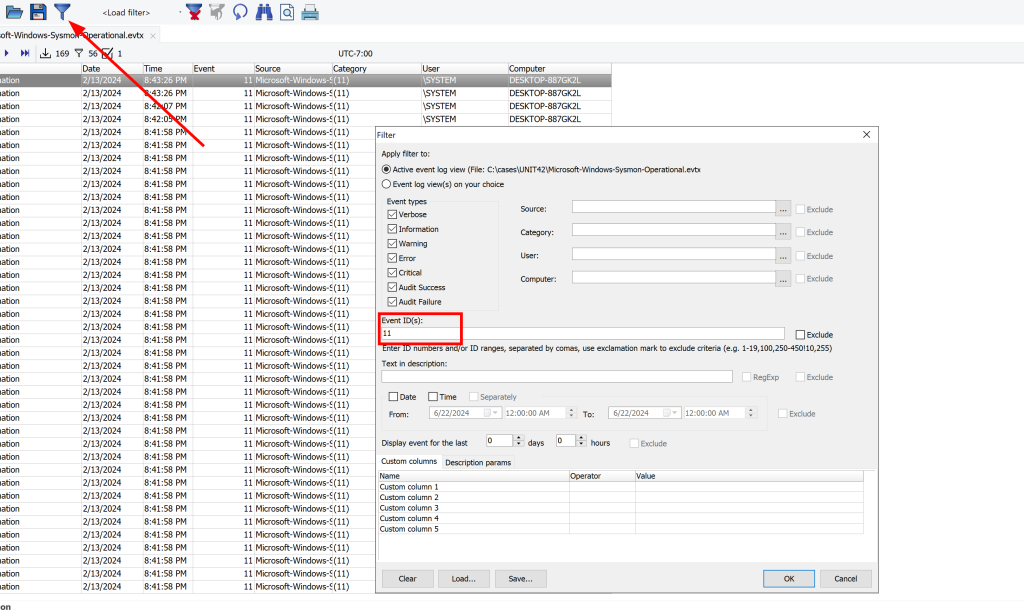
After doing this we can see that there are a total of 56 events that contain event ID 11
What is sysmon event 11?
Records when a file is created, which can be used to track the drop of malware or temporary files by attackers.
Our next question is asking us to find the malicious process that was created we can do this using event ID 1
What is sysmon event ID 1
Logs the creation of a process, providing insights into the execution of potentially malicious or unexpected software.
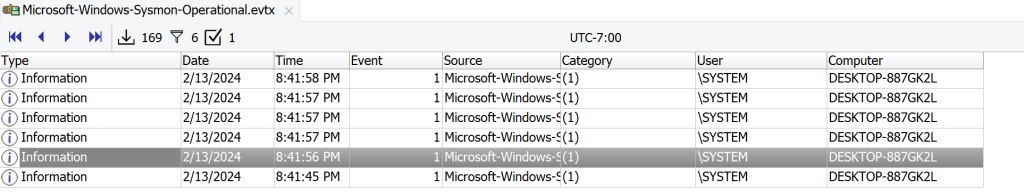
After filtering for sysmon event ID 1 we get 6 results we can look through these one by one to see if we see anything suspicious
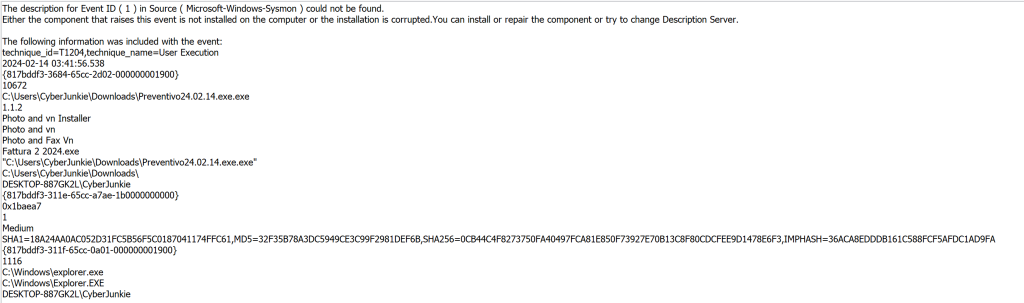
At first glance this looks out of the ordinary, and we can check virus total or other online virus repositories to see if the hash provided to us in the description flags as anything malicious.
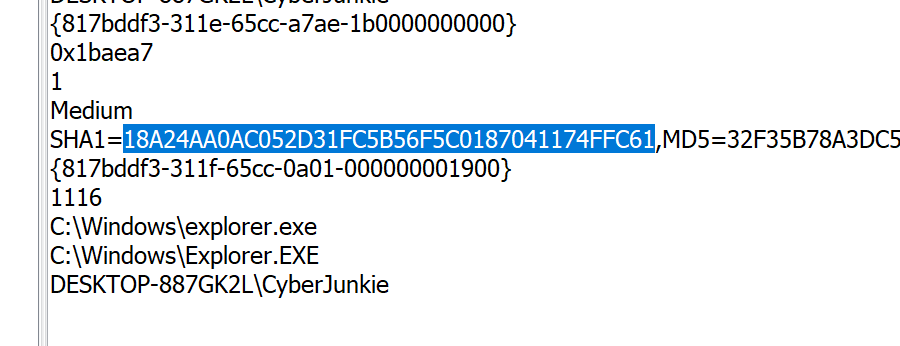
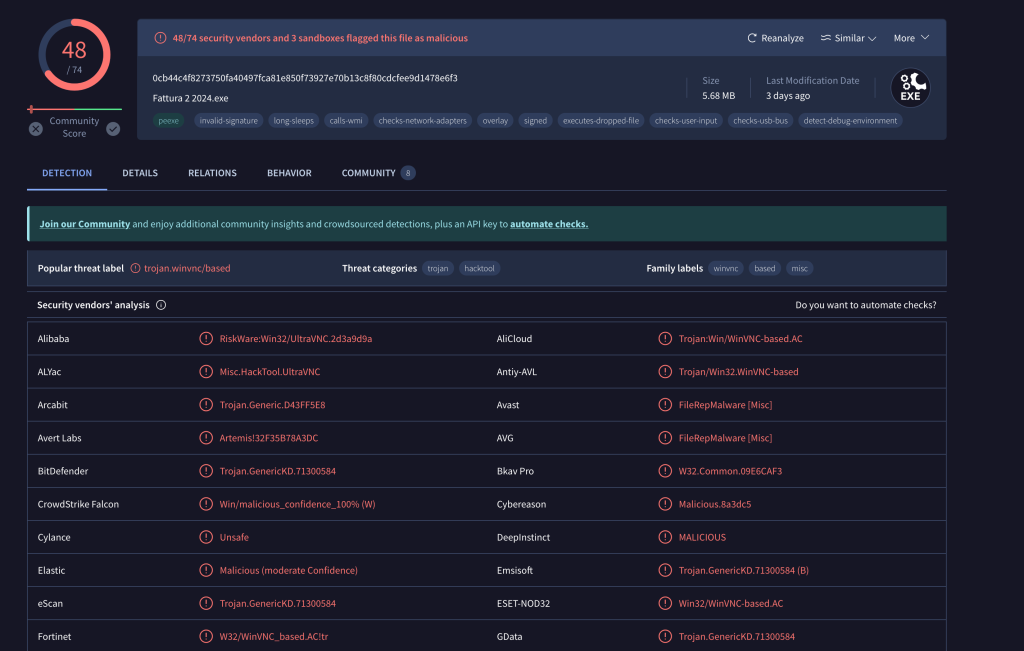
After taking our hash we can see that this is the malicious process that was spawned on the system and looks to be part of the UltraVNC hack
Tracing Malware distribution
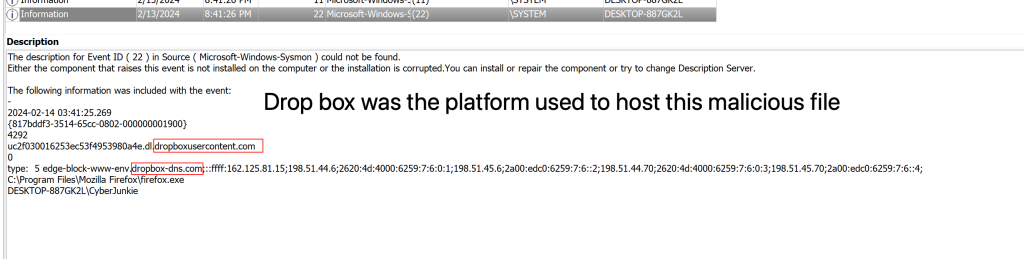
Our next task is to see which cloud drive was used to distribute the malware, to do this we will take a look at sysmon event ID 22. Attackers frequently exploit the use of cloud hosting services as a platform for their payloads. This is due to the common whitelisting and permissibility of the domain by company proxies.
What is sysmon event ID 22?
Event ID 22 can be used to look for any DNS Queries made by the system.
We aren’t going to filter for any specific event ID; we will start analyzing the events from the oldest available event. If we see events related to the malicious file being created, we will look for an Event ID 22 event surrounding that event.
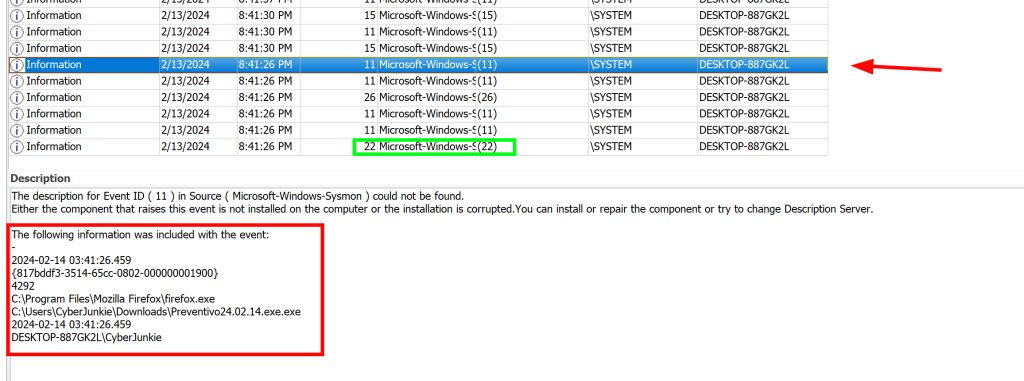
Here we can see event ID closely placed before our initial file creation related to the malicious`Preventivo24.02.14.exe.exe` process
Timestamp Manipulation
The next task/question we will address is related to finding evidence of timestamping
What is timestamping & How to find evidence of it
Timestamping is a defense evasion technique used by attackers to alter the creation or modification dates of files, making them appear older or more legitimate. This can help malicious files blend in with legitimate files and avoid detection by security measures that rely on file dates to identify suspicious activity.
Filter for Event ID 2. This event ID records any file creation time changes on any files on the system.
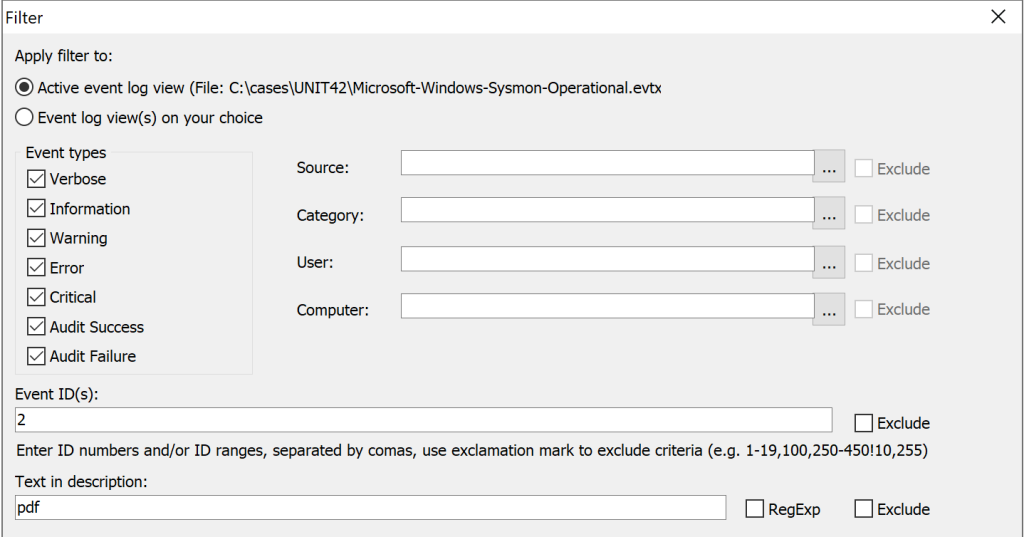
After Filtering for sysmon event ID 2 and include `PDF` in the filter in the “Text in description section” as was mentioned in the original question it gives us a single event log
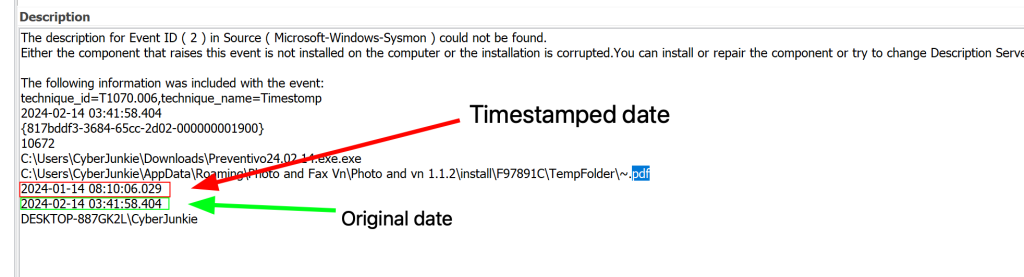
Taking a look at it, we can see that the date was timestamped to look like it was on the machine a month before it actually showed up.
Malicious Files dropped on disk
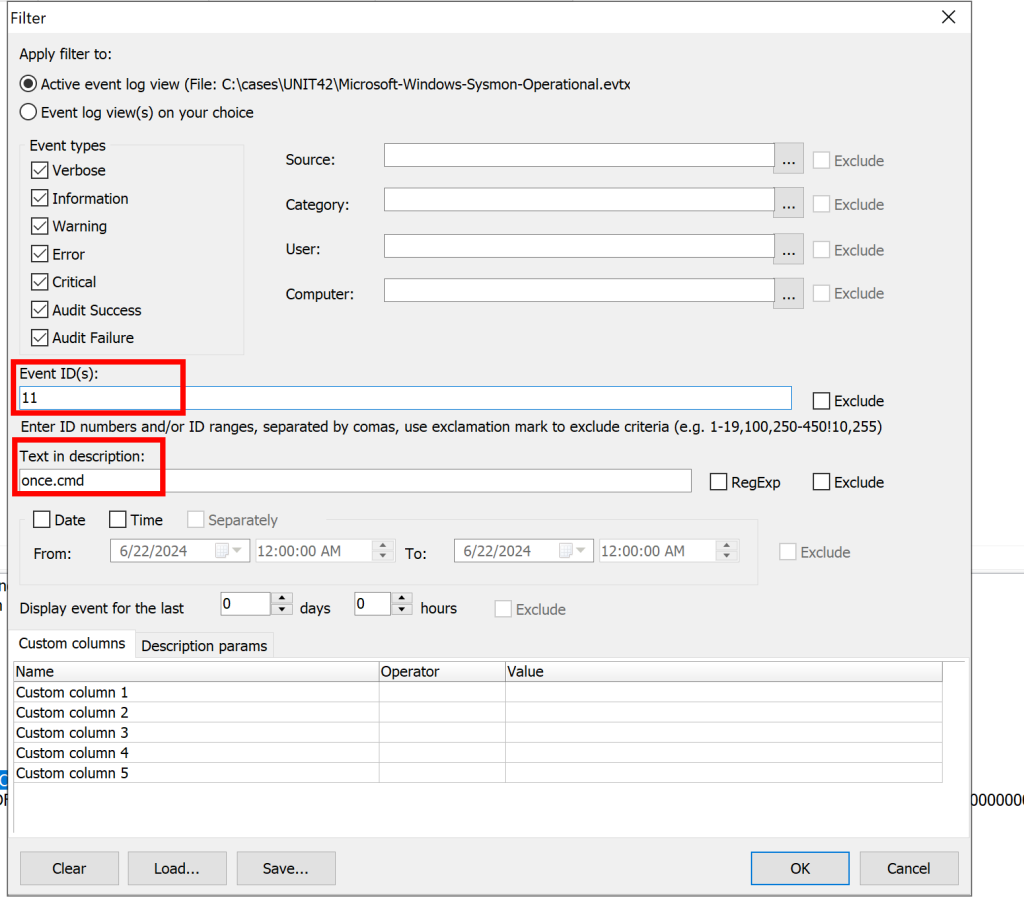
The next question in our investigation is looking for the location of “once.cmd” a file from the malicious file that was dropped on the disk and easy way to look for this is both with file creation and just looking for the name of it since it was provided to us
The filter we used
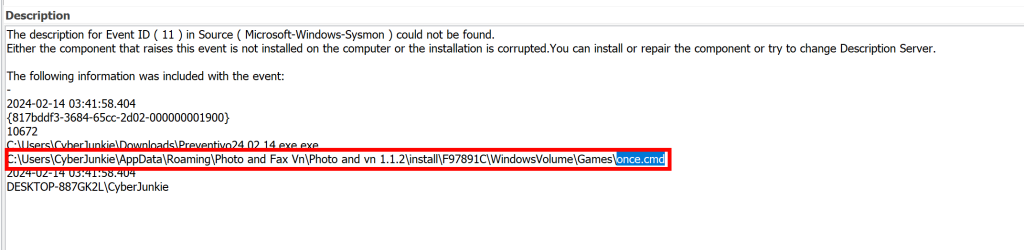
And the earliest example of this showing up in our logs has this path that it was saved too
‘C:\Users\CyberJunkie\AppData\Roaming\Photo and Fax Vn\Photo and vn 1.1.2\install\F97891C\WindowsVolume\Games\once.cmd’
Network Indicators of Compromise
here we will look for both the domain and the IP address that was attempted to be contacted by our malicious process
First we will look for domains contacted using Sysmon ID 22
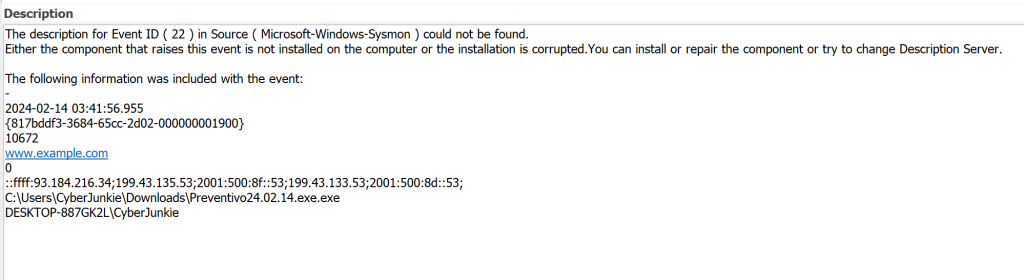
Here we can see the malicious process attempting to reach out to a dummy domain, most likely to check internet connectivity
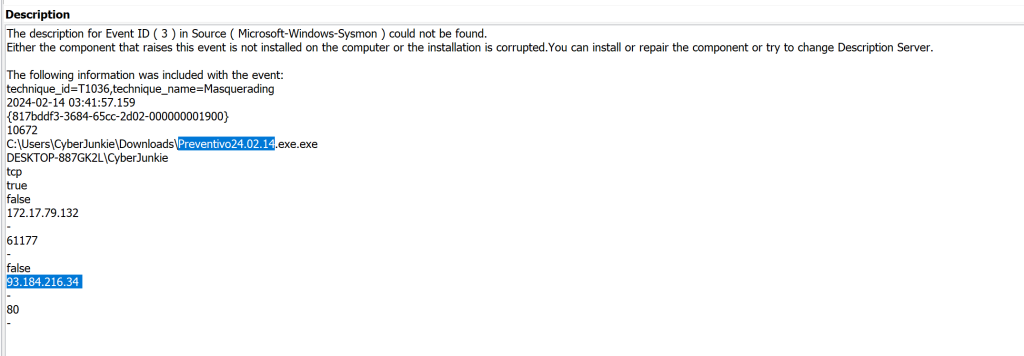
Moving on to other attempts at network connectivity we will use sysmon event id 3 to see if it attempted to reach out to any other IP addresses
Process Termination
The final question we will answer is when was the malicious process terminated on the infected machine
What is Sysmon event ID 5
Event ID 5 (Process Termination)
This event is logged when a process terminates. It provides detailed information about the process that has ended, helping in tracking the lifecycle of processes on the system.
Filtering for event ID 5 and our malicous process name inside ELEX
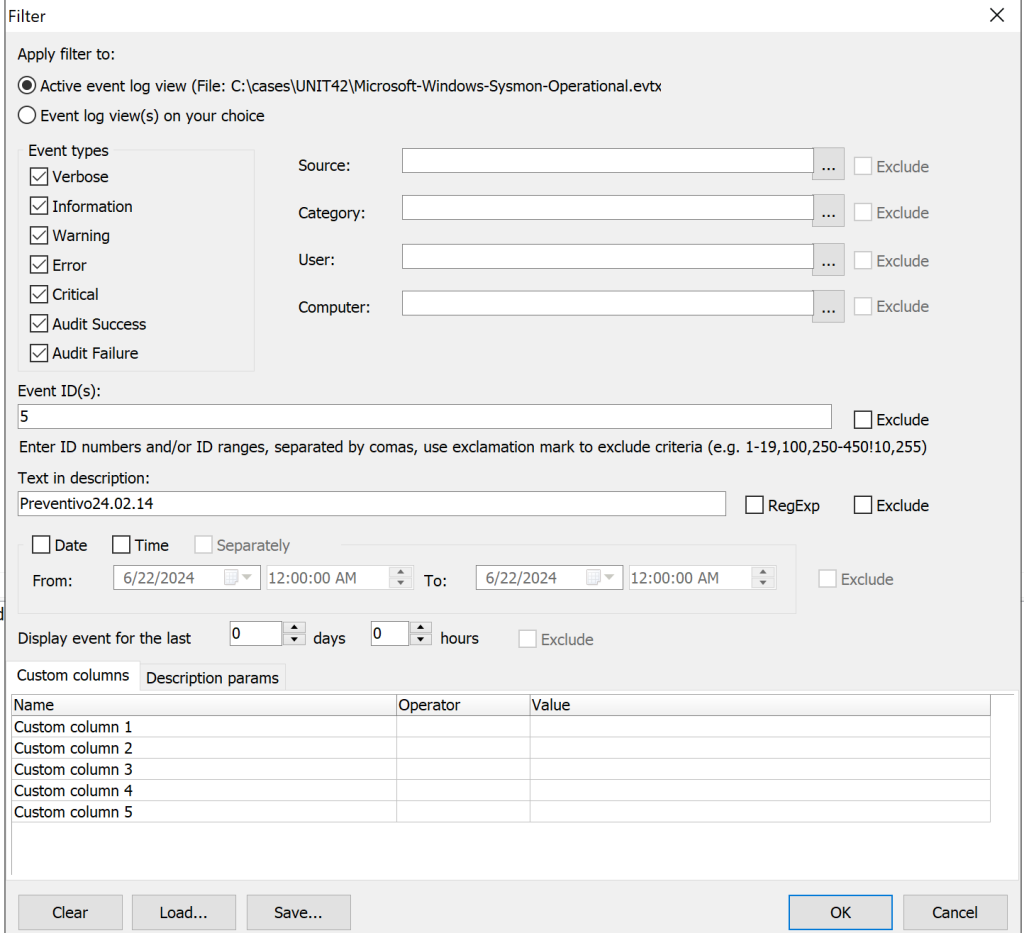
This shows us a single event and gives us the time of the process termination
Conclusion
Wrapping up, this Sysmon lab based on the UltraVNC campaign by Unit42 highlights the power of Sysmon in detecting and analyzing suspicious activities. By diving into Sysmon logs and understanding Event IDs, we can piece together the puzzle of an attack, from initial access to malicious actions. This hands-on experience not only sharpens our analytical skills but also reinforces the importance of detailed logging in cybersecurity. Staying vigilant and proficient with these tools is key to defending against evolving threats.
If you would like more information regarding sysmon, event log explorer you can visit the links below to learn more
https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon
