Splunk Boss of the SOC (BOTS v1)
Splunk Boss of the SOC (BOTS) is a challenging capture-the-flag (CTF) competition designed specifically for security analysts. This competition is built around Splunk, the leading software platform for real-time operational intelligence, and involves using Splunk to solve a variety of security incidents. BOTS v1, the first edition of this competition, allows participants to engage with Splunk’s capabilities by tackling real-world security problems through a gamified experience.
The first version of BOTS is set in a scenario involving Wayne Enterprises, a large, fictional corporation that finds itself the victim of several cybersecurity attacks. Among these, the most prominent is a website defacement incident, where the attackers have replaced the company’s homepage with a message from the notorious hacking group “Po1s0n1vy”.
We are going to jump into the scenario, use Splunk to sift through mountains of log data to uncover the details of the attack. This includes identifying the initial breach points, understanding the scope of the compromise, tracking the attackers’ lateral movements within the network, and finally, piecing together the timeline and methodology of the attack.
Initial Alert and Response
In this scenario the alert was originally received via Gotham City Police Department (GCPD. GCPD has found evidence online (http://pastebin.com/Gw6dWjS9) that the website www.imreallynotbatman.com hosted on Wayne Enterprises’ IP address space has been compromised.
First thing we want to do is confirm the report, contain any systems that have been effected, remediate the issues and then continue with on going monitoring.
Investigation Phase
- Identifying the Threat Actors: Discuss how you identified the Po1s0n1vy group as the suspects.
- Tools and Techniques Used: Describe the tools and techniques used to gather information about the attack, such as web logs, DNS records, and IP tracing.
Subsections for Key Questions:
- IP Address Identification: How you determined the likely IPv4 addresses involved in the attack.
We are going to start with a simple search to find the ip associated with the attack on our webserver
index=botsv1 source="stream:http"looking through the src_field in Splunk shows us a couple different IP addresses, but one stands out above them all and is a red flag in terms of how much it is talking to our server to investigate this more we are going to add it to our search
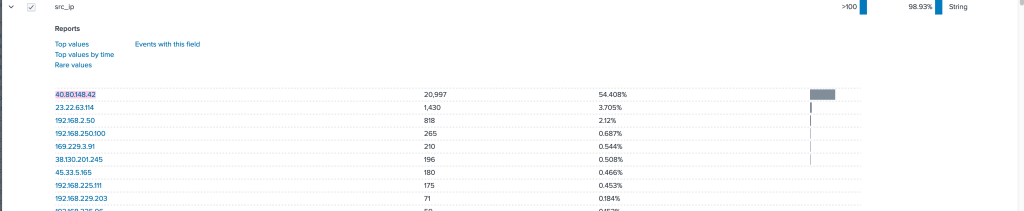
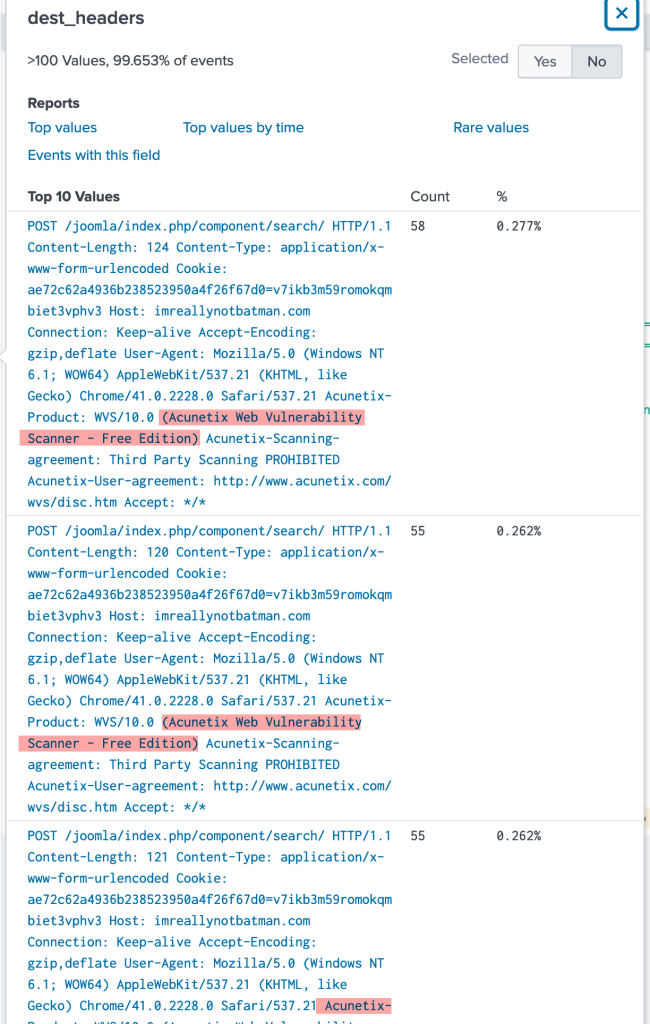
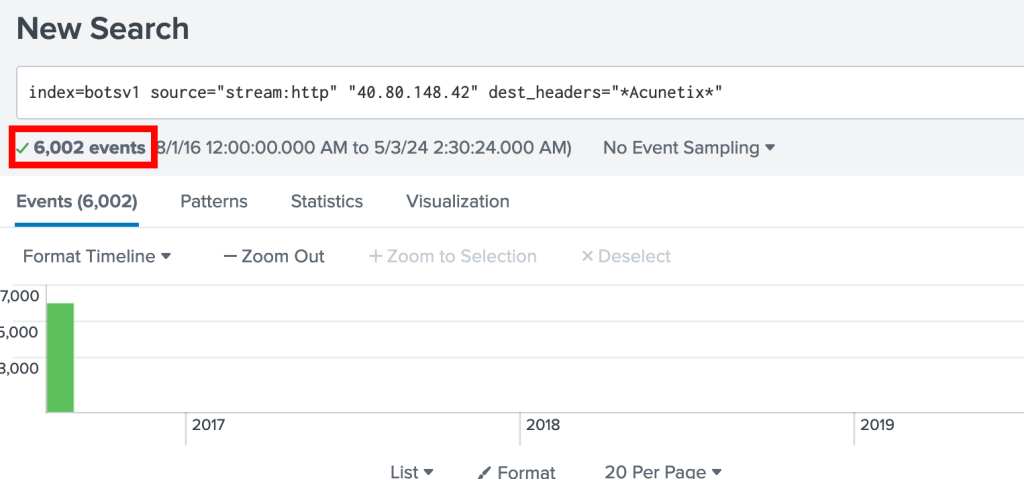
When looking at our headers field in the communication with the suspected IP we see the use of a vulnerability scanned called acunetix being used over 6,000 times
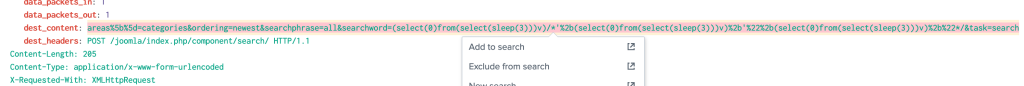
When looking at the first log that shows up we can see they were attempting SQL injections against our web server
Looking for more proof of defacement on our website we will have to switch the flow of traffic to find the IP of our web server
index=botsv1 imreallynotbatman.com src_ip="40.80.148.42"The source IP will change to the web server IP of imreallynotbatman.com. Pulling the defacement picture file from the attacker’s website because the server has already been compromised by the attacker.
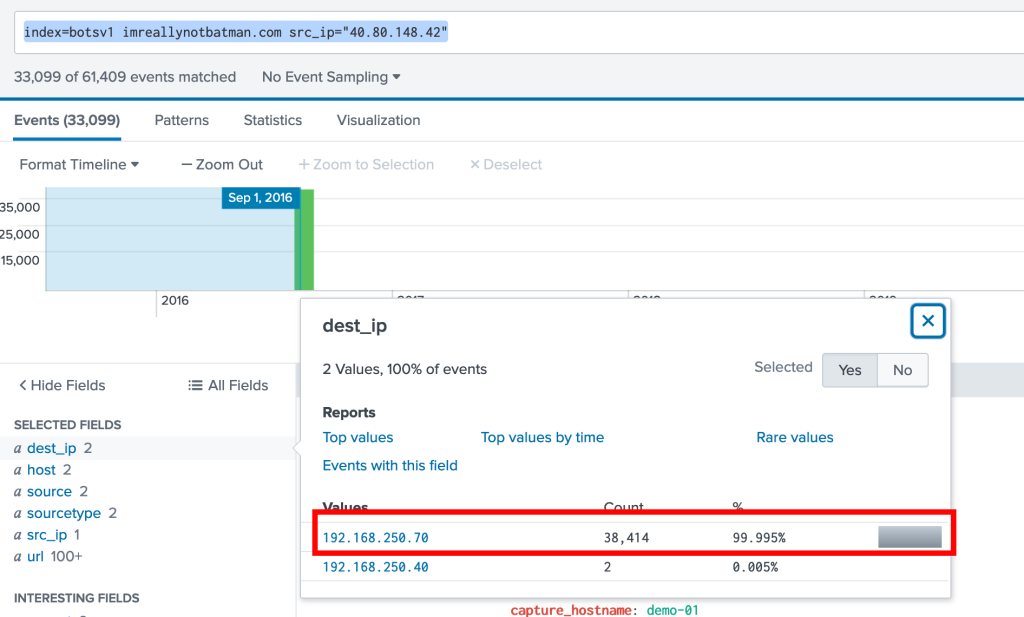
This will give us the target IP of the attackers 192.168.250.70
Looking for the web server they used to upload the file that defaced our website we are going to use the stats command in Splunk to look at which URLs are contacting imreallynotbatman.com
index=botsv1 c_ip="192.168.250.70"
| stats count by url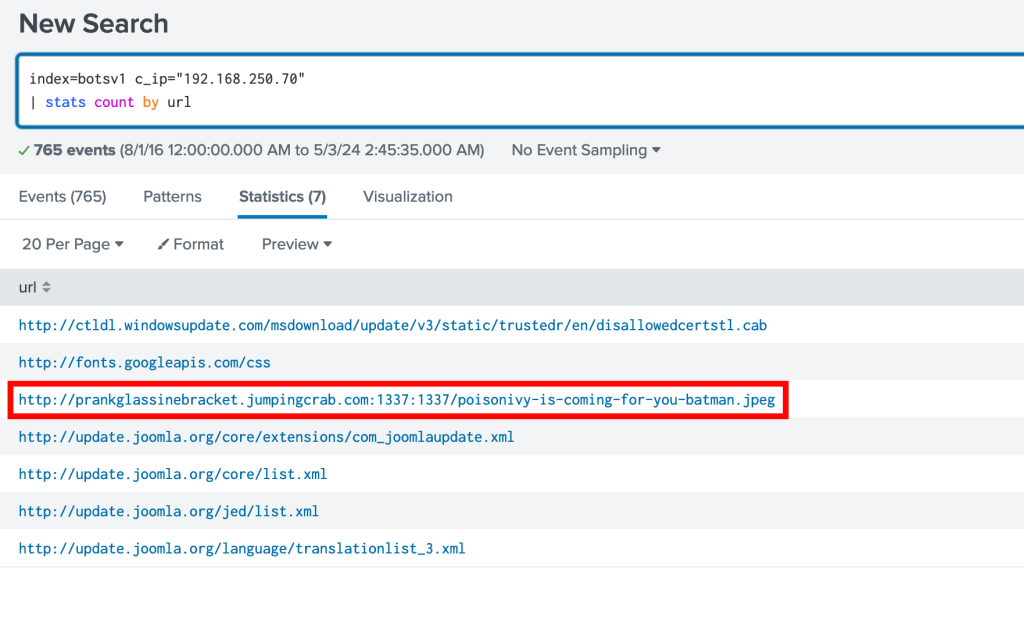
And we can see the file responsible for the defacement image uploaded to the imreallynotbatman.com website
Deep Dive into Specific Attacks
This attack used dynamic DNS to resolve to the malicious IP. The domain mentioned previously was the Fully qualified domain name from the DNS attack looking up the IP from our logs associated with the FQDN on virus total .
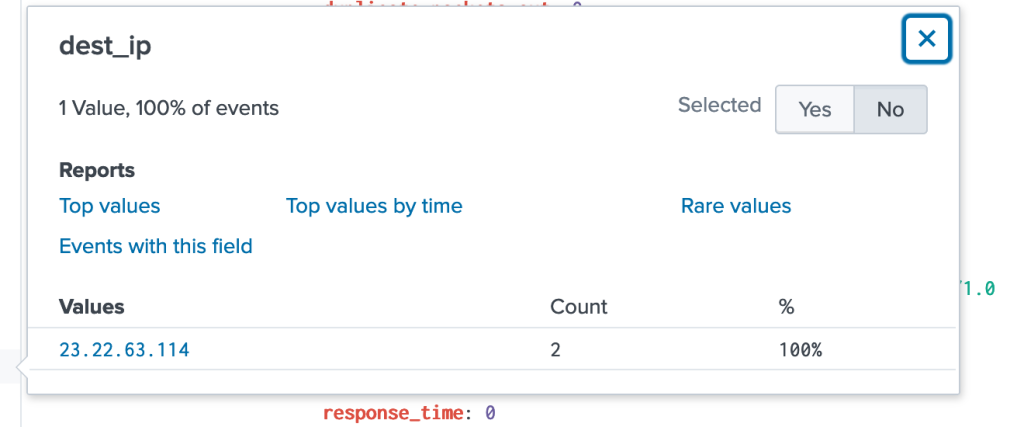
The malicious IP tied to the FQDN and used as the pre-stage for the attack on imreallynotbatman.com is 23.22.63.114 as shown above
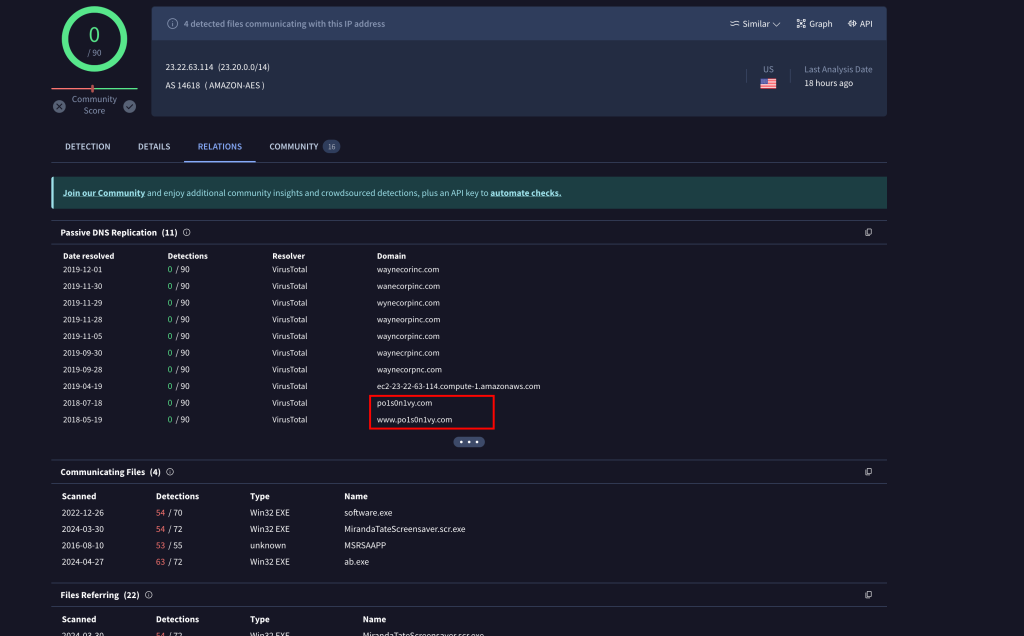
We can now confirm that this IP is related to the po1son1vy group
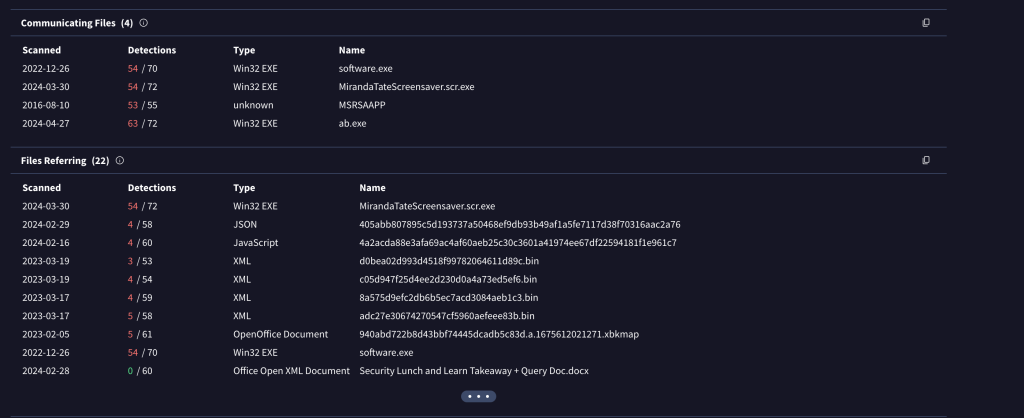
when scrolling down further in virus total we can see the malicious software related to po1son1vy
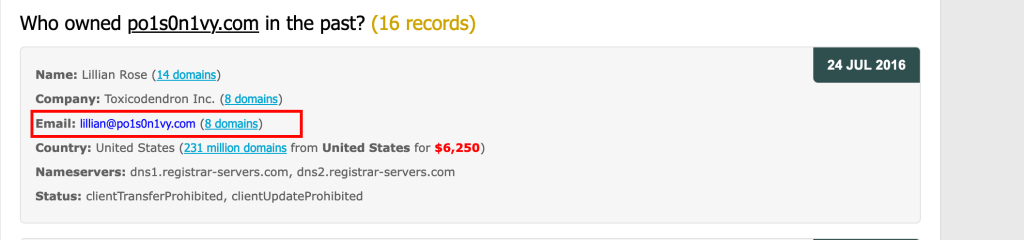
Using a google search of “Pos1on1vy APT” on google brings us to the whoxy results about the APT group and we can see the email used to register the domain is “lillian@po1s0n1vy.com”
Moving back to Splunk and looking for any lateral movement from the IP
index=botsv1 23.22.63.114
When looking at the form_data field in Splunk we can see that there is a bruteforce attack going on against our admin account
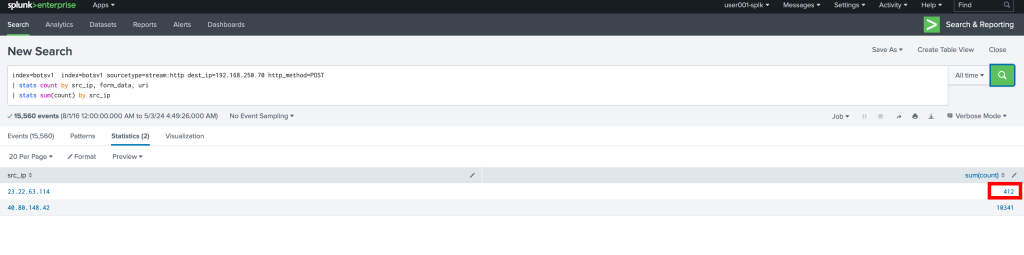
index=botsv1 index=botsv1 sourcetype=stream:http dest_ip=192.168.250.70 http_method=POST
| stats count by src_ip, form_data, uri
| stats sum(count) by src_ipUsing the Splunk query above we will be able to see how many attempts for the bruteforce attack was done by this malicious IP
Using the Splunk query below we can see what password allowed them access to our admin account
index=botsv1 sourcetype=stream:http dest_ip="192.168.250.70" http_method=POST uri=/joomla/Administrator/index.php
| rex field=form_data "passwd=(?<password>\w+)"
| sort _time
| table _time src_ip password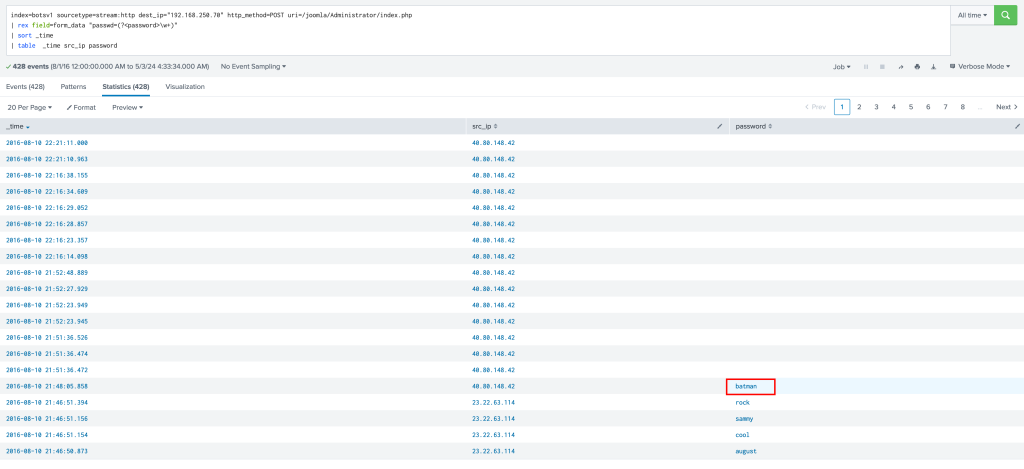
Moving onto actions on objectives and file uploads post compromise on our webserver
index=botsv1 sourcetype=stream:http dest_ip="192.168.250.70" http_method=POST multipart/form-data *.exe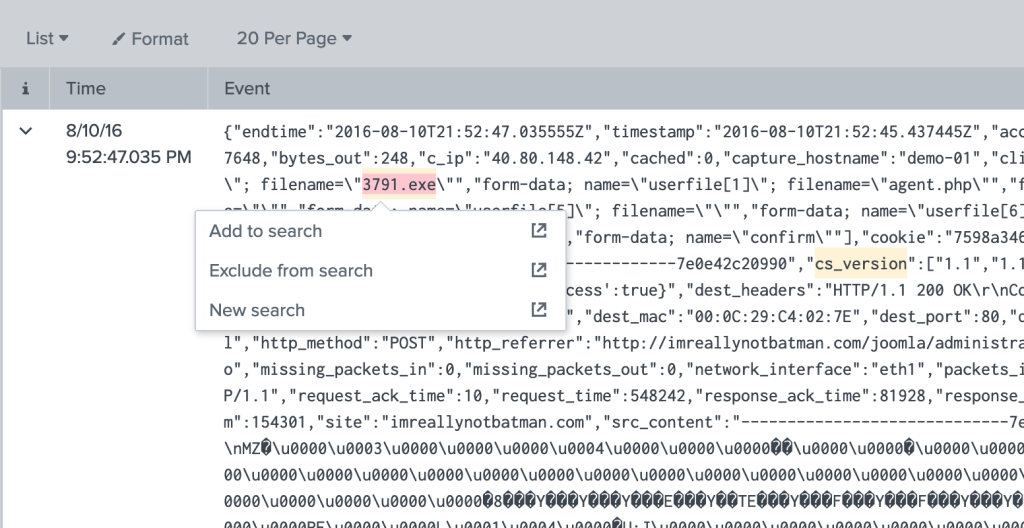
We can see that 3791.exe was uploaded to our server to look for the md5 hash up on virus total we need to change the source type to “sysmon” with the name of the executable as our keyword search.
index=botsv1 sourcetype=sysmon 3791.exe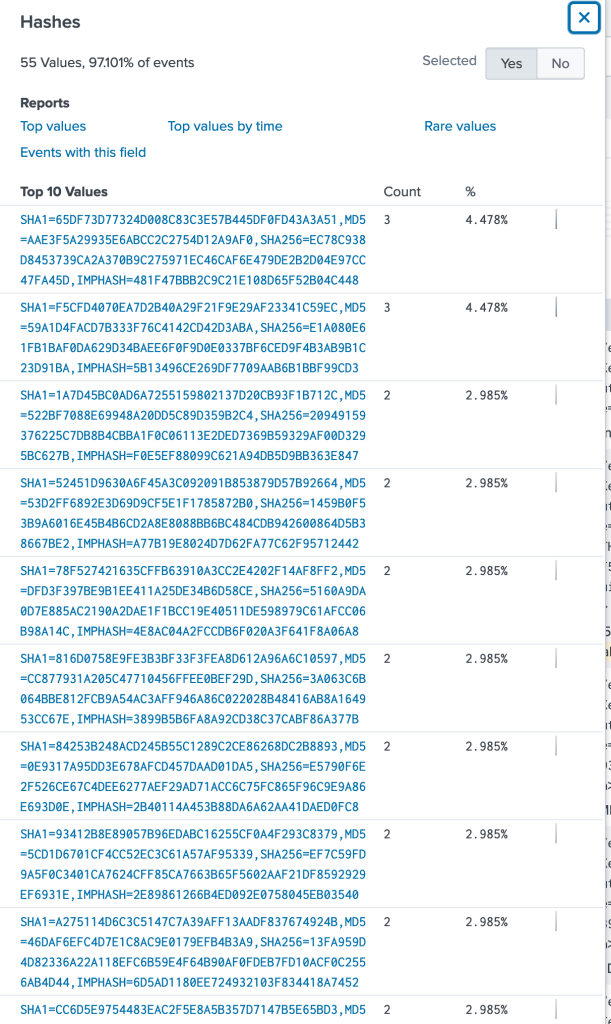
with our results clicking on the hashes field we get a handful of results and im not sure exactly which one is related to the 3791.exe program so moving over to command line and selecting the one that mentions this program will help narrow down our results
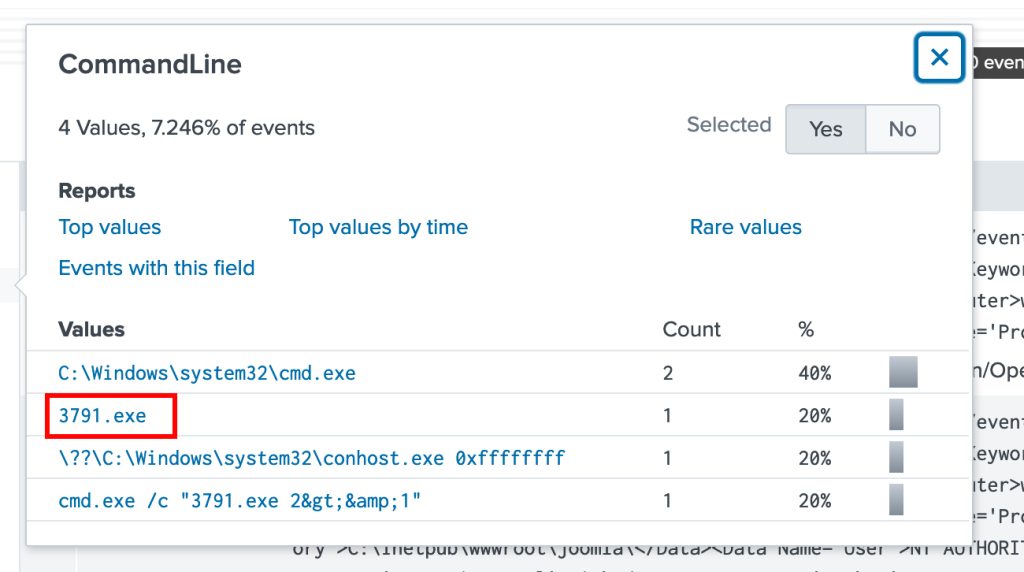
Now we get the correct hash result
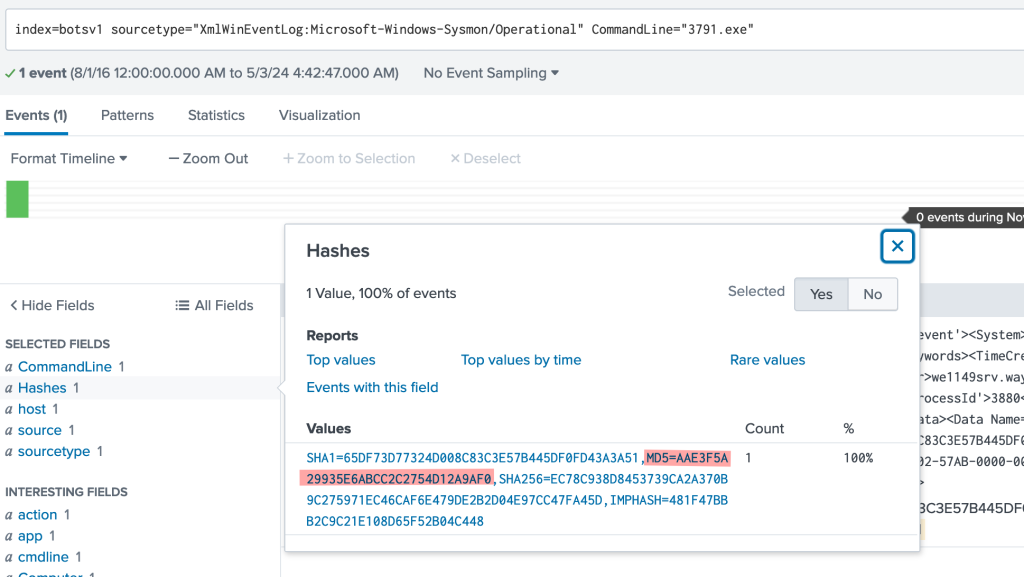
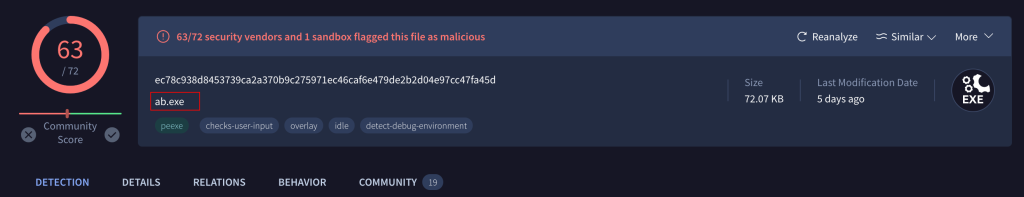
taking the hash “AAE3F5A29935E6ABCC2C2754D12A9AF0” and looking it up on virus total tells us that its “ab.exe” something that we saw earlier when looking for the ip address assocaited with the staging attack
Mitigation and Prevention
Actions to be Taken: Upon confirming the defacement of www.imreallynotbatman.com, immediate actions should be taken to mitigate the attack and prevent further damage.
The website should be temporarily taken down to remove the defaced content and to prevent public exposure to the unauthorized changes.
Network access logs should be scrutinized to identify and block the IP addresses associated with the attackers, thereby cutting off their access to our systems.
Security patches should be applied to the known vulnerabilities that were exploited during the attack, and stronger firewall rules were set up to enhance the perimeter defense.
Thank you for reading along and taking time to follow through the investigation of the pos1on1vy APT’s attacks on Wayne corps network
