“It takes 20 years to build a reputation and a few minutes of cyber-incident to ruin it.”
Stephane Nappo.
an alert has surfaced within the Security Operations Center (SOC) indicating a possible insider threat. The suspect employee’s workstation has been secured and examined. During the memory analysis, the Senior DFIR Analyst succeeded in extracting several intriguing URLs from the memory. These are now provided to us for further analysis to uncover any evidence, such as indications of data exfiltration or contact with malicious entities.
In this Digital forensics scenario we will be using OSINT to track down evidence of an insider threat, the simulation based on real life events is provided by Hack The Box under the name of “Constellation”
Chapter 1: The Discovery
The senior DFIR analyst has provided us some information after examining the suspect employees machine

Looking in the files given to us, we have IOC’s provided.
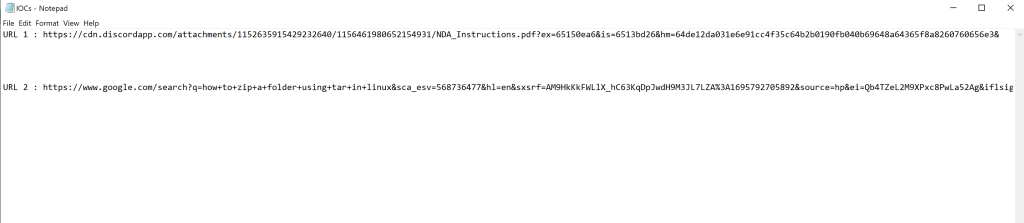
Clicking on the text file provided shows us the IOC’s. IT contains two links, one which looks to be a discord attachment and the other a Google search string.
Chapter 2: Following the Trail of Digital Bread Crumbs
Starting out we are going to open the discord attachment link and see where that brings us
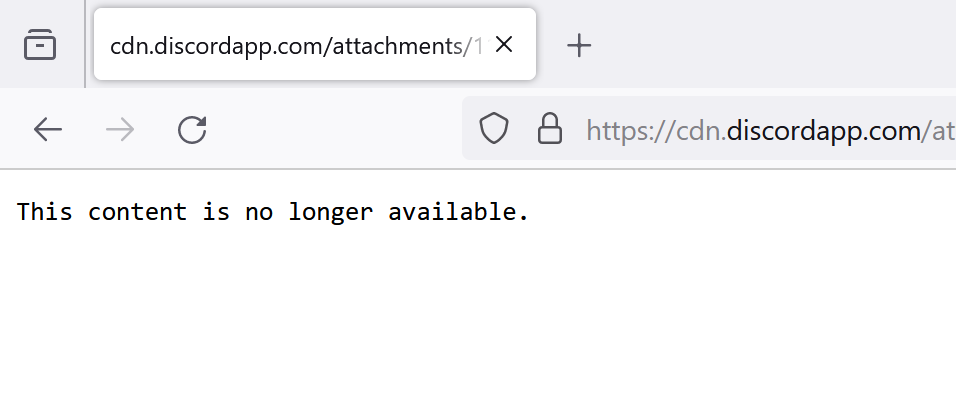
It shows us a dead link, and trying to view the page source shows us the same thing. Nothing hidden here.
We can try to open it in the Wayback Machine to see if we can get an archived version of the link. I have a bookmarklet set up to open the page I’m currently on in the way back machine. (setting up OSINT bookmarks and Bookmarklets post linked here)
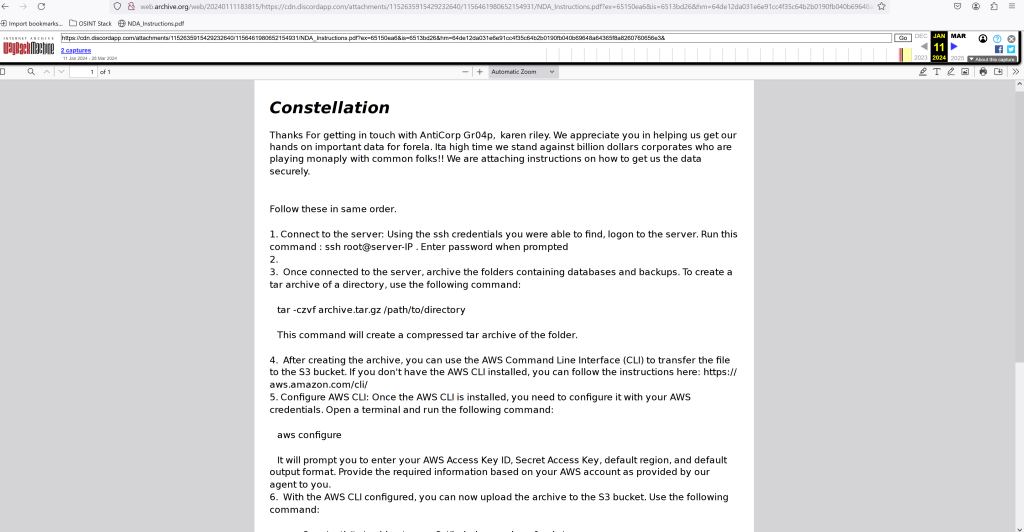
Opening the link in the way back machine we see a PDF that looks to be a set of instructions from a threat actor to our suspected employee with steps in order to set up malicious programs on our AWS servers (looks to be ransomware from the name of it)
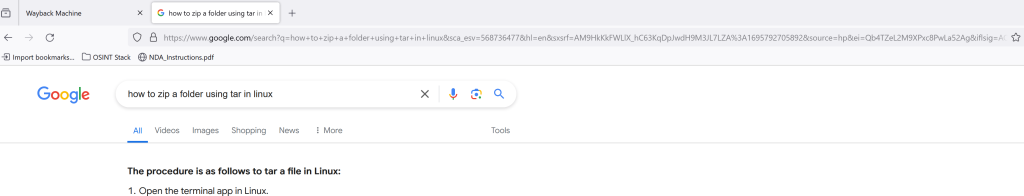
Google search string
Chapter 3: Unraveling the Timeline
To help us Decode the URL’s presented and help us get a timeline of events we will use Unfurl. Unfurl takes a URL and expands (“unfurls”) it into a directed graph, extracting every bit of information from the URL and exposing the obscured. It does this by breaking up a URL into components, extracting as much information as it can from each piece, and presenting it all visually
Starting with the discord link
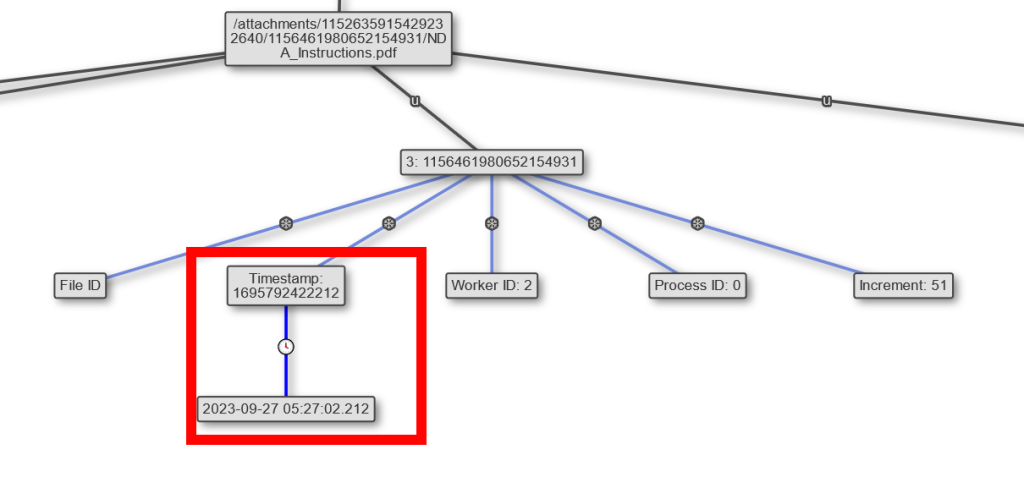
We can see the time that the attachment was sent at here.
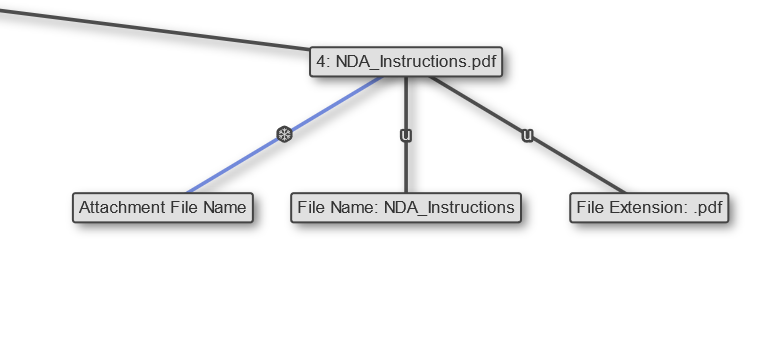
And information about the attachment, this also confirms the PDF that was shown on the Wayback Machine when we were looking at it.
Now on to the Google link
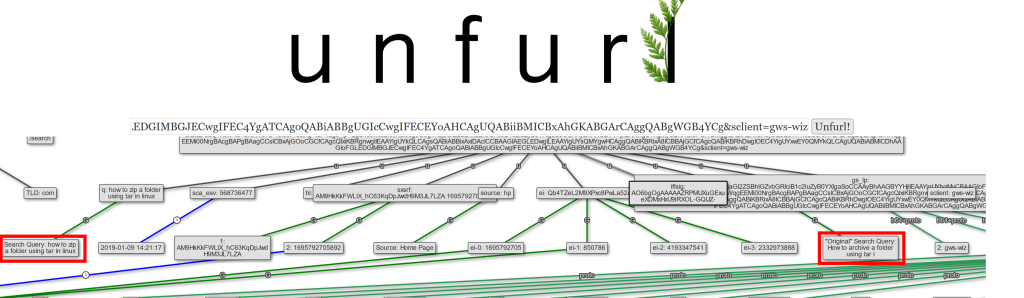
In this portion of the URL we can see the original search query and the current search query, the Original ‘How to archive a folder using tar’ and ‘how to zip a folder using tar in Linux’ being the current
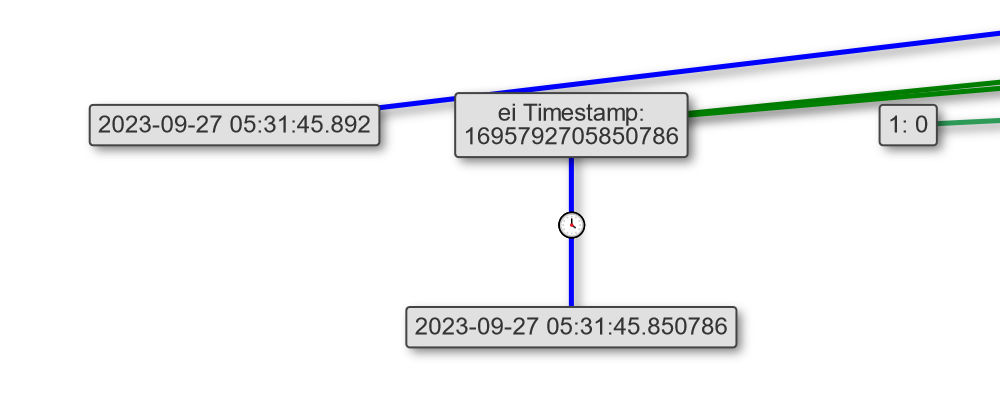
We can also the date the search was executed which comes shortly after the file was sent over discord less than 5 minutes between the file being sent and the employee trying to figure out how to unzip / zip a file using tar on Linux
Chapter 4: Exposing Insider Collaboration
Let’s look closer at the PDF sent to our insider threat over discord
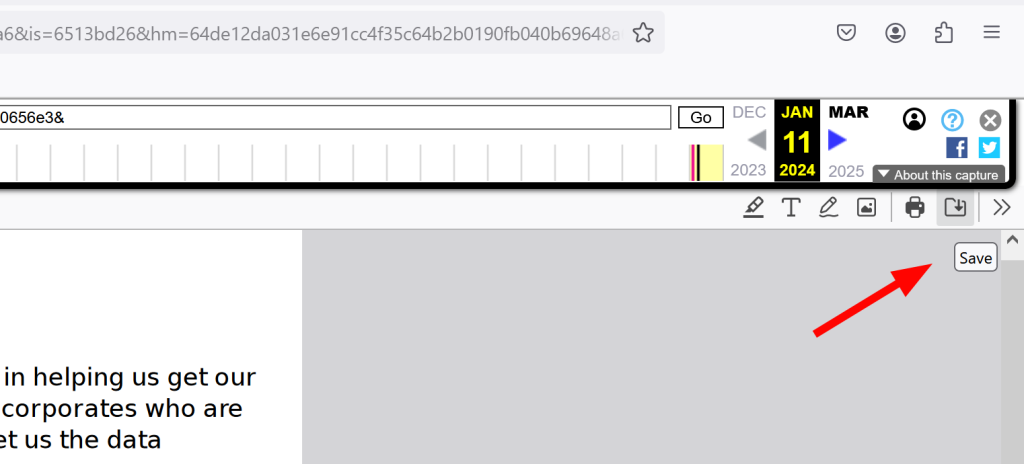
We are going to want to save it from the Wayback Machine to download it and then upload it to an EXIF metadata viewing site to get more information from the PDF
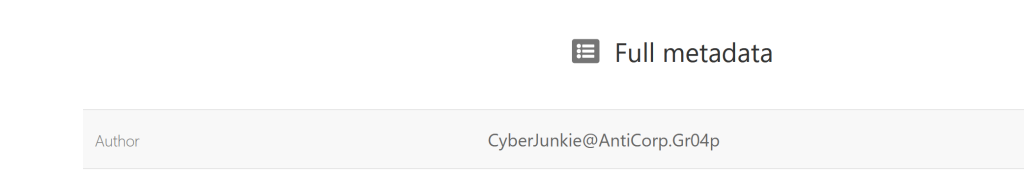
Here we can see the email of the author as well as to who the PDF was made out to
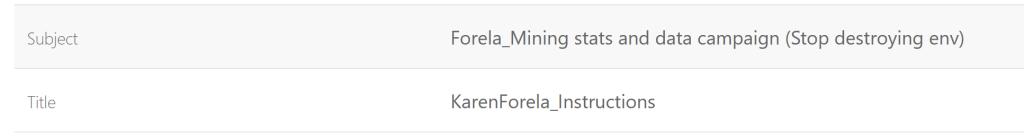
Karen is our insider threat, but we still need to track down our threat actor.
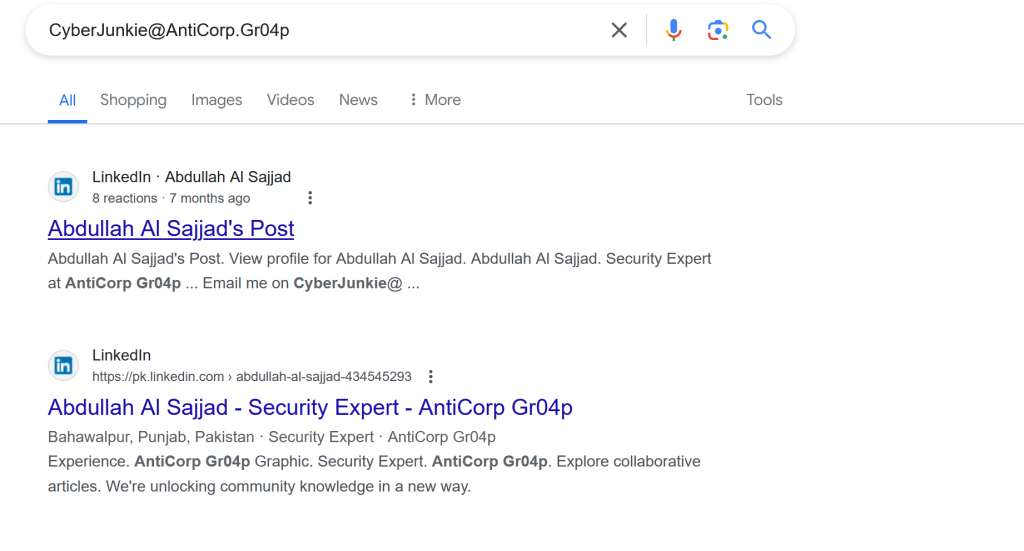
Looking up the author of our PDF we get brought up a few results most notably a LinkedIn page.
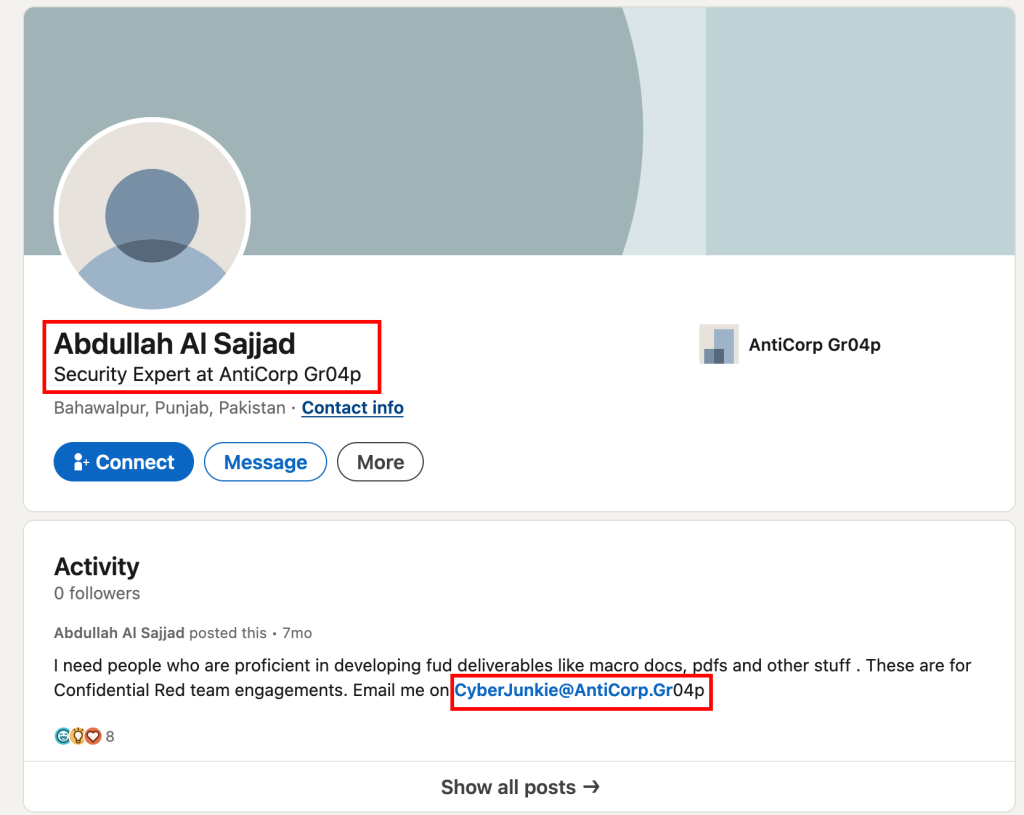
Here we can see our threat actor’s name, location and a post of him looking for malware engineers possibly to help him more with organized cybercrime
Chapter 5: Securing the Network and Preventing Future Threats
Insider threats can lead to substantial data breaches, intellectual property theft, and financial losses. In the future, Forela should improve their security measures against insider threats. This situation could have been stopped before it started by.
- Comprehensive Employee Training: Implement regular training programs to educate employees about the signs of insider threats, the importance of following security protocols, and the consequences of security breaches. This can also include training on how to handle sensitive information securely.
- Robust Access Controls: Strengthen access control mechanisms to ensure that employees have access only to the data and systems necessary for their roles. Implement strict authentication and authorization protocols, and regularly review access permissions.
- Behavioral Monitoring: Use advanced monitoring tools to detect unusual activities that could indicate insider threats. This includes monitoring access logs, data usage patterns, and other relevant security metrics.
