Hook, Line, and Sinker
Phishing is a form of social engineering, a tactic where cyberattackers manipulate individuals into giving up confidential information or performing actions that will compromise security. In phishing, attackers exploit human psychology and trust by posing as reputable entities or individuals in communications like emails or messages or over the phone (Vishing). The aim is to create a sense of urgency, fear, or trust to prompt the target to reveal sensitive data, click on malicious links, or download harmful software.
Phishing always seems to target the weakest link in internet connectivity, the human part of it. it’s not just individuals falling for phishing attacks but some of the largest cooperations in the world.
The Nordea Bank Incident (2007)
Sweden’s largest bank, Nordea, was outsmarted by phishers rather their customers. They sent emails that seemed genuine, prompting customers to download what was claimed to be anti-spam software. In reality, it was a Trojan called “haxdoor” that installed a keylogger on users’ computers. This move redirected customers to a fake bank website, where the criminals stole their login credentials. Counting for a loss of over 7 million kronor
Sony Pictures Breach (2014)
Sony Pictures experienced a massive security breach. Hackers stole over 100 terabytes of confidential information, causing significant financial and reputational damage. They managed this by sending deceptive emails that appeared to come from co-workers, with attachments that were anything but safe. Another notable tactic was a fake Apple ID verification email, which helped the attackers discover re-used passwords that were also used for Sony’s networks.
Facebook & Google’s $100 Million Mistake
Sony Pictures experienced a massive security breach. Hackers stole over 100 terabytes of confidential information, causing significant financial and reputational damage. They managed this by sending deceptive emails that appeared to come from co-workers, with attachments that were anything but safe. Another notable tactic was a fake Apple ID verification email, which helped the attackers discover re-used passwords that were also used for Sony’s networks.
Today we are going to walk through some phishing emails and do analysis on them
Effective phishing email analysis involves a comprehensive approach to identify, analyze, and mitigate phishing attacks. Here are some key components considered in effective phishing email analysis:
- Email Header Analysis: This involves examining the technical data in the email header to identify the true source of the email. Looking at fields like the return path, received from, and originating IP address to trace the email’s journey and verify the sender’s authenticity.
- Content Examination: The body of the email is scrutinized for malicious content, including suspicious links, attachments, and the presence of social engineering tactics. Content analysis may use natural language processing to detect urgency, impersonation, and other signs of phishing.
- Link and Domain Analysis: URLs within the email are analyzed to check their legitimacy. This involves verifying the domain against known blacklists, examining the URL for misleading characteristics, and sometimes using sandbox environments to see where the link actually leads.
- Attachment Analysis: Attachments are scanned using antivirus software / Online repositories of malware like Virus total and sandboxing technologies to detect malware and other malicious payloads without opening them on a network-connected computer.
- Sender Reputation: The reputation of the sender’s email domain and IP address is checked using various reputation services that track the history of the sending source in terms of email security threats.
- User Training and Awareness: While not a direct part of email analysis, training users to recognize and report phishing attempts is crucial. Effective analysis often involves reviewing user-reported emails to continually adapt to new phishing tactics.
- Integration with Security Policies: Effective analysis also includes the integration of findings into broader security measures, such as updating firewalls, email gateways, and endpoint protection based on the threats identified.
These components, combined into a systematic approach, make up effective phishing email analysis, helping organizations to prevent breaches and mitigate the risks associated with email-based threats.
The source of the phishing / scam emails we are going to be looking at today are provided in part by THM from the “Snapped Phish-ing Line” module. Based on real-world occurrences and past analysis, this scenario presents a narrative with invented names, characters, and events. Then we are going to take a look through the inbox of one of my old emails to see what’s floating around in the spam folder.
Email 1:
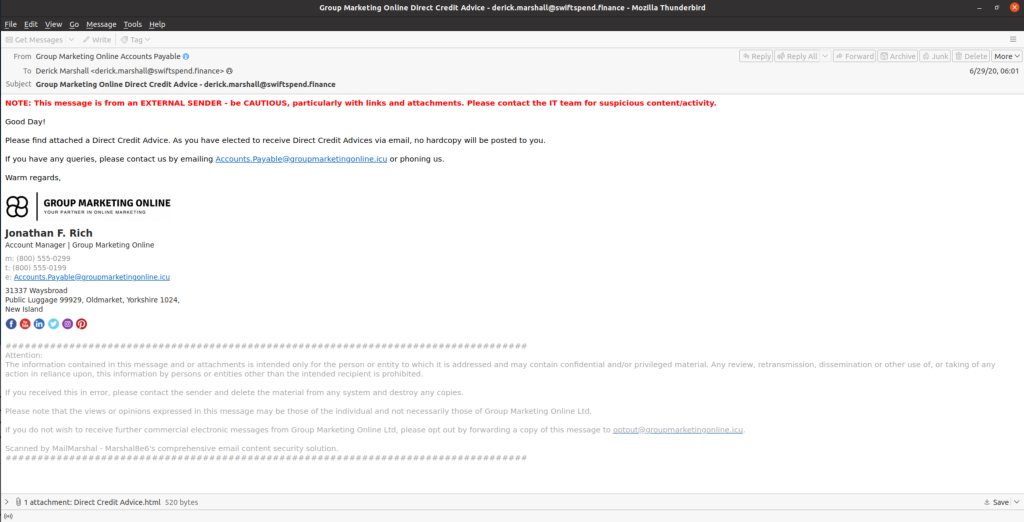
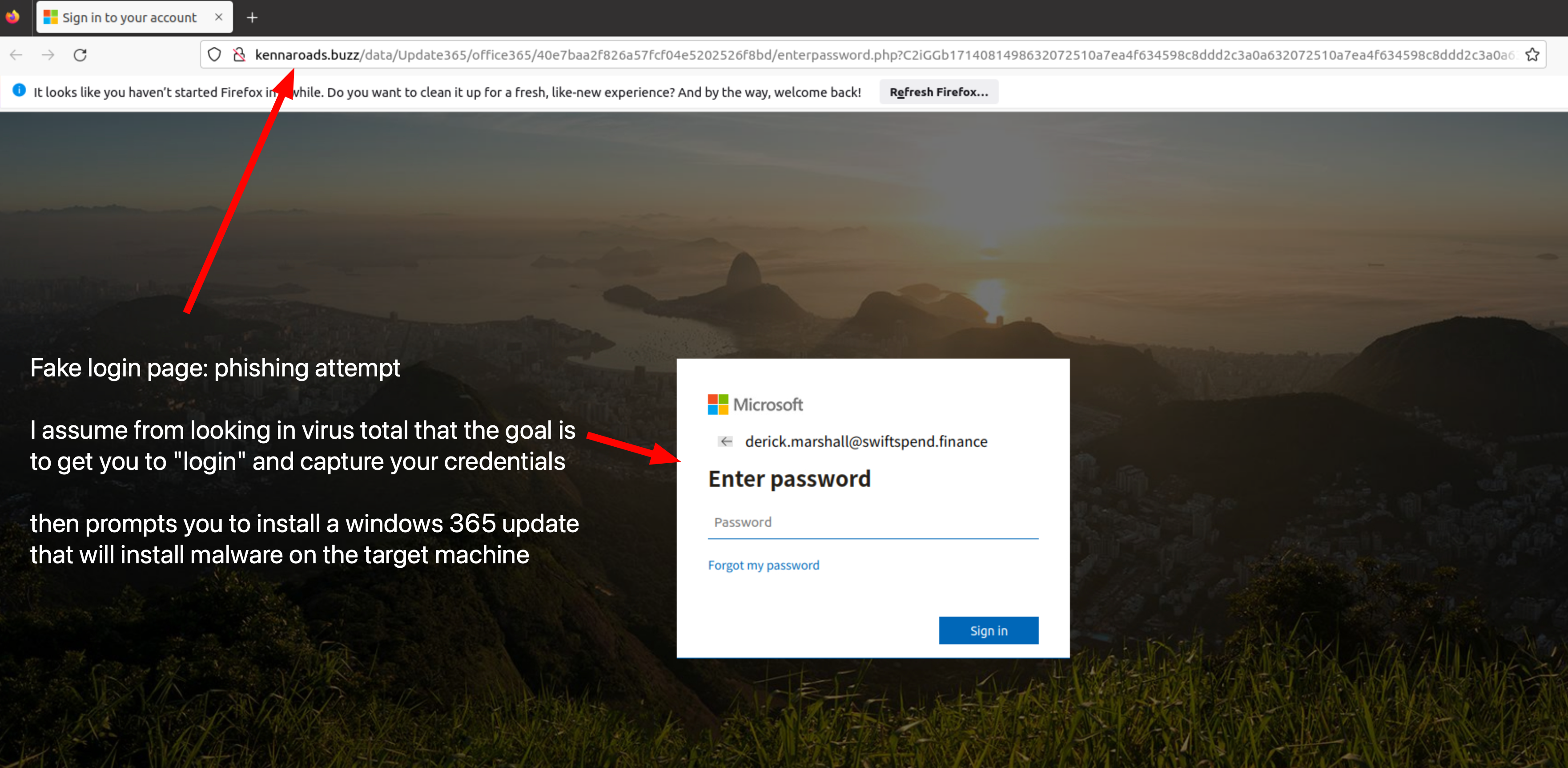
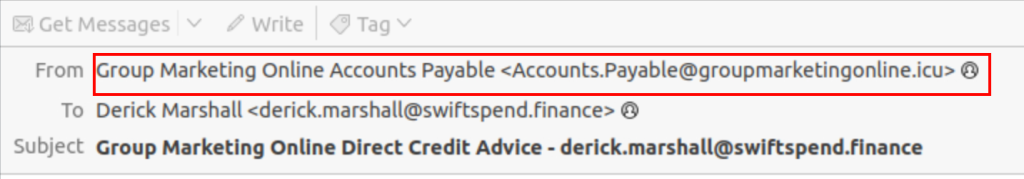
Here is the first email we have to analyze it seems to be an invoice sent from “group marketing online” and contains an attachment. the first thing that stands out is the big red notification telling us that it’s from an external sender
When looking at the sender email address we can see that it has an unusual top-level domain (.icu). An email address with a “.icu” domain could potentially be suspicious. The generic top-level domain (TLD) could be something to purchase to be cheap and set up quickly by threat actors
Let’s save this attachment and open it up in a text editor (this is sandboxed in a different machine than my host)
saving and opening the email in the text editor gives us some more information
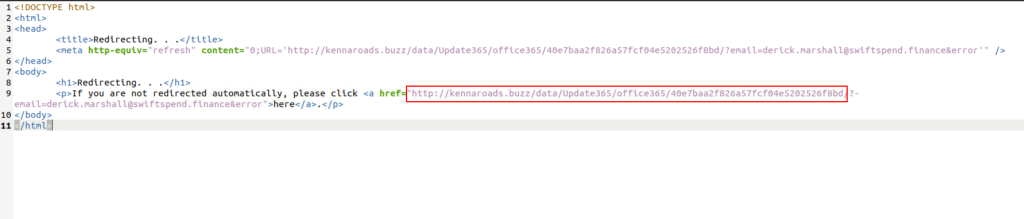
here we can see that it tries to open a webpage, plugging this URL into urlscan.io shows us a handful of redirects upon clicking on the link. this often conceals malicious links & is common in phishing attacks
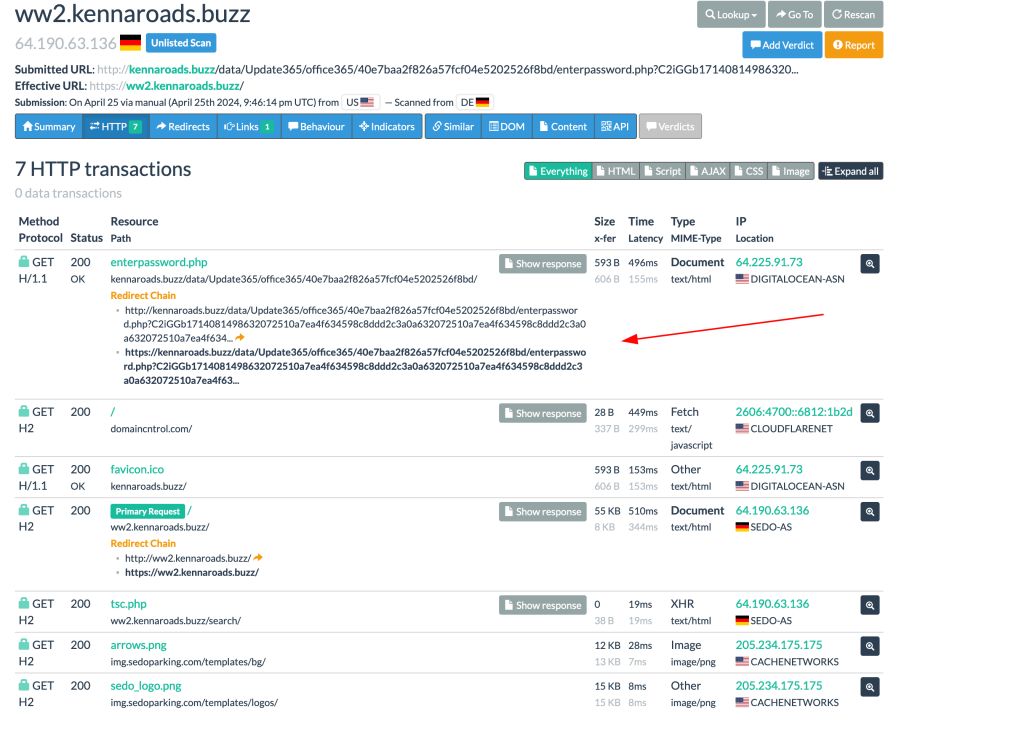
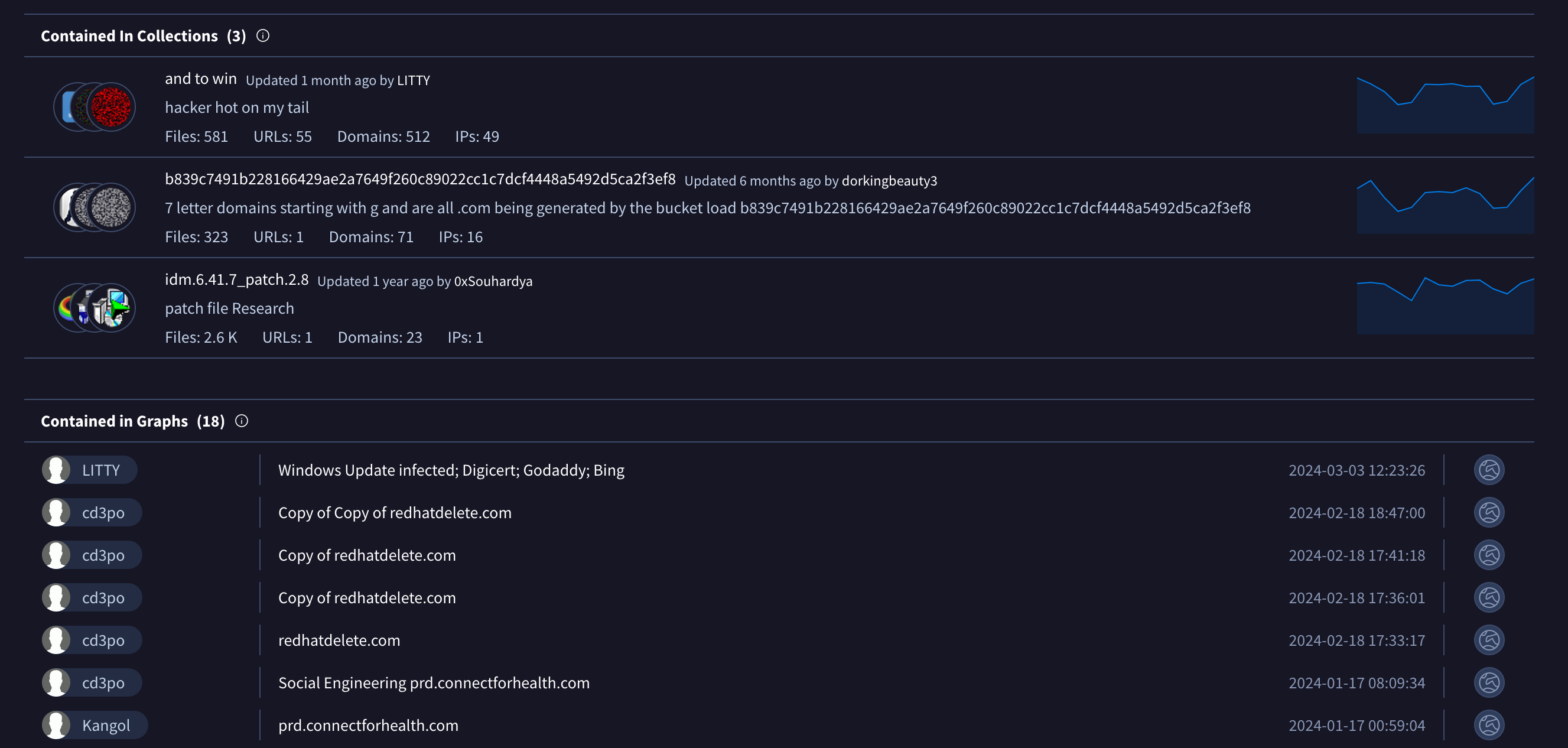
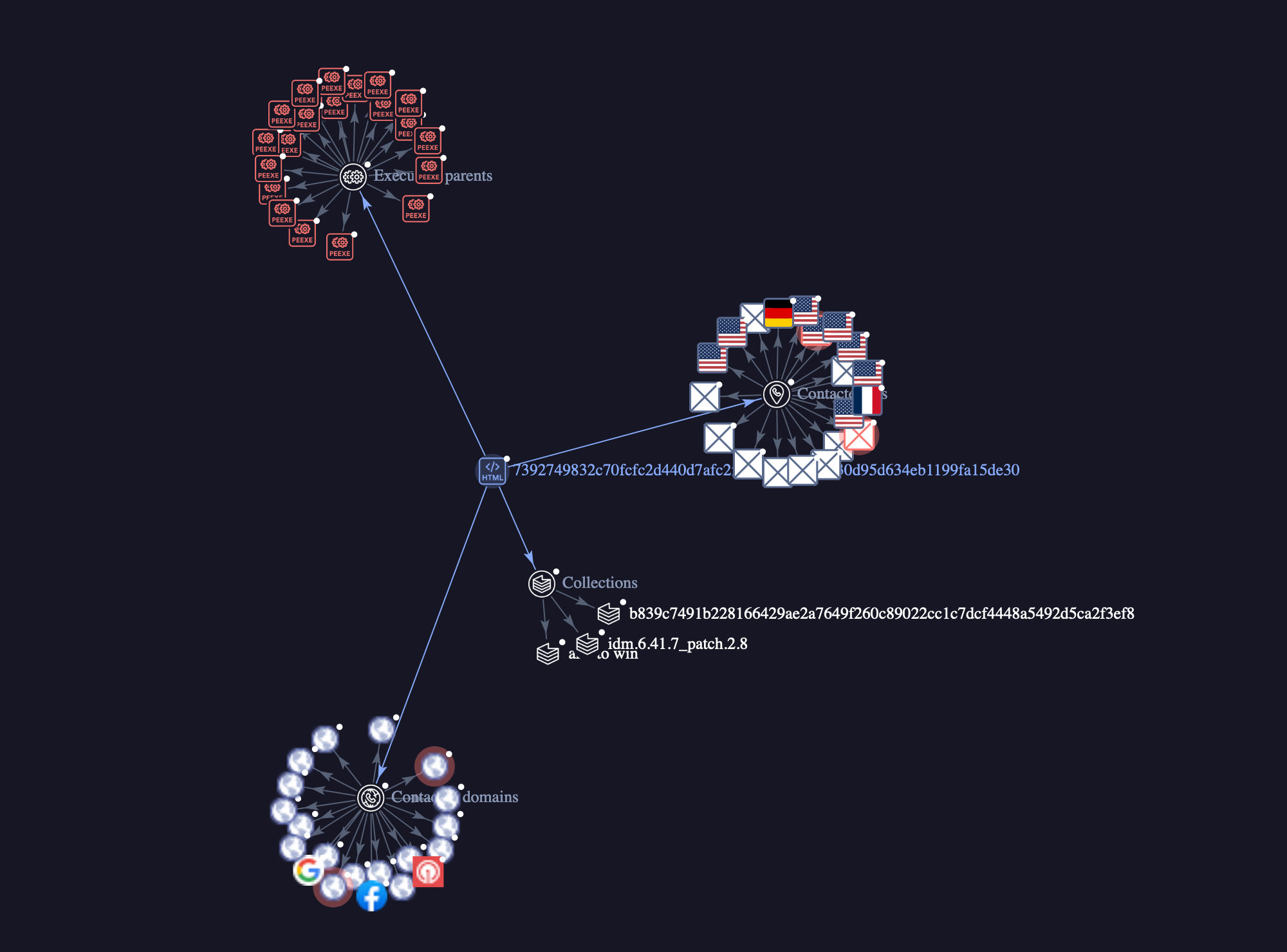
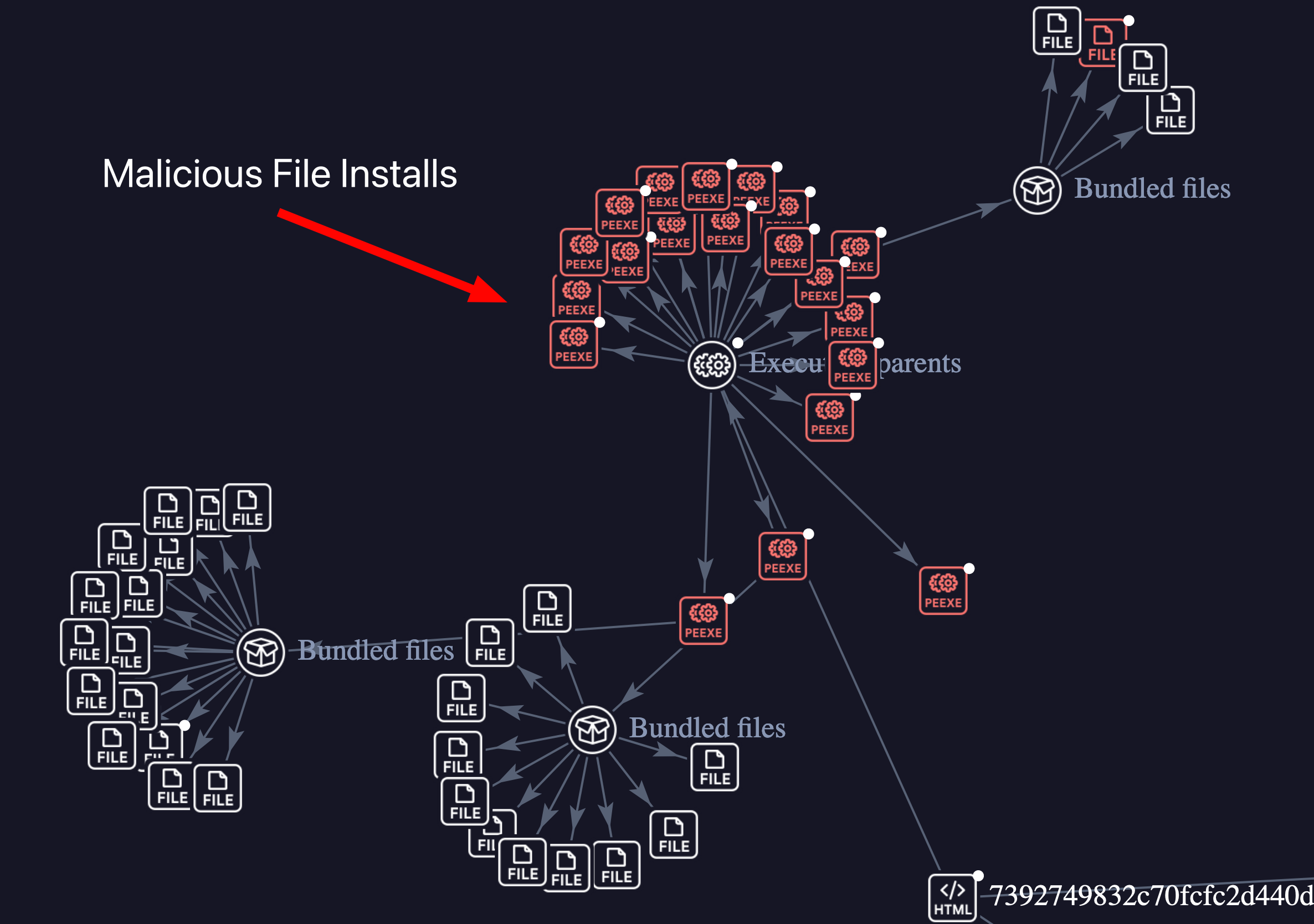
Clicking around to get more information from urlscan gives us a resource hash, we can plug this into virus total and see what the webpage is up too
Shown in the images above virus totals response about the resource hash, some users saying it’s a part of social engineering. The next images detail the graph provided from virus total and likely attack chain, and the final image showing us opening the web page in a sandbox confirming our suspicions about the email being malicious
let’s take a closer look at the attackers website
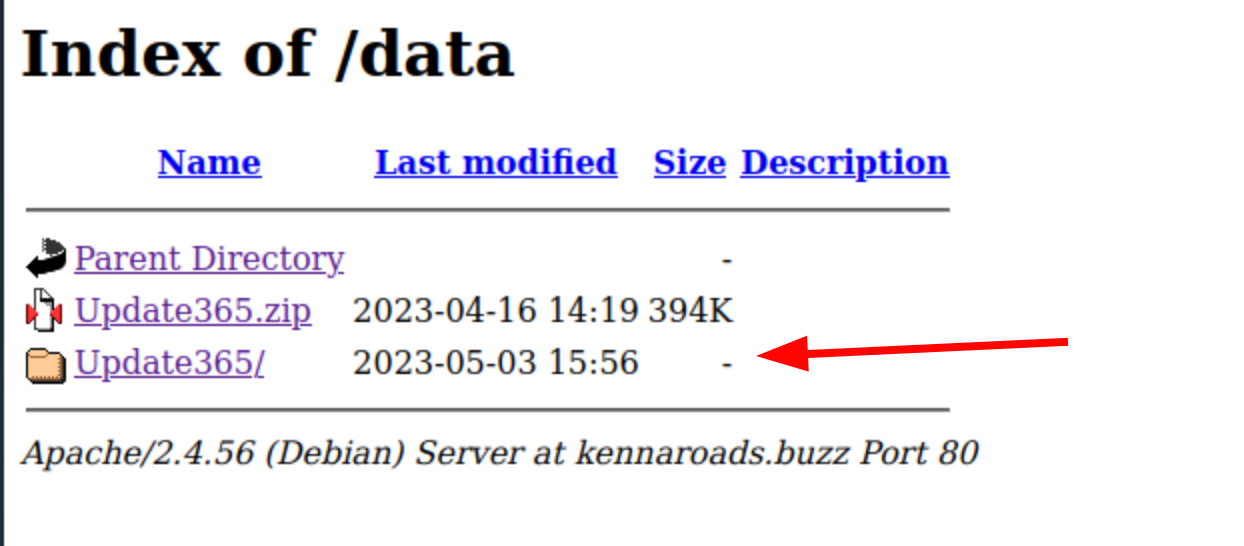
visiting the site hxxps[://]kennaroads[.]buzz/data. we can see that it does host a zip file titled “update365.zip”
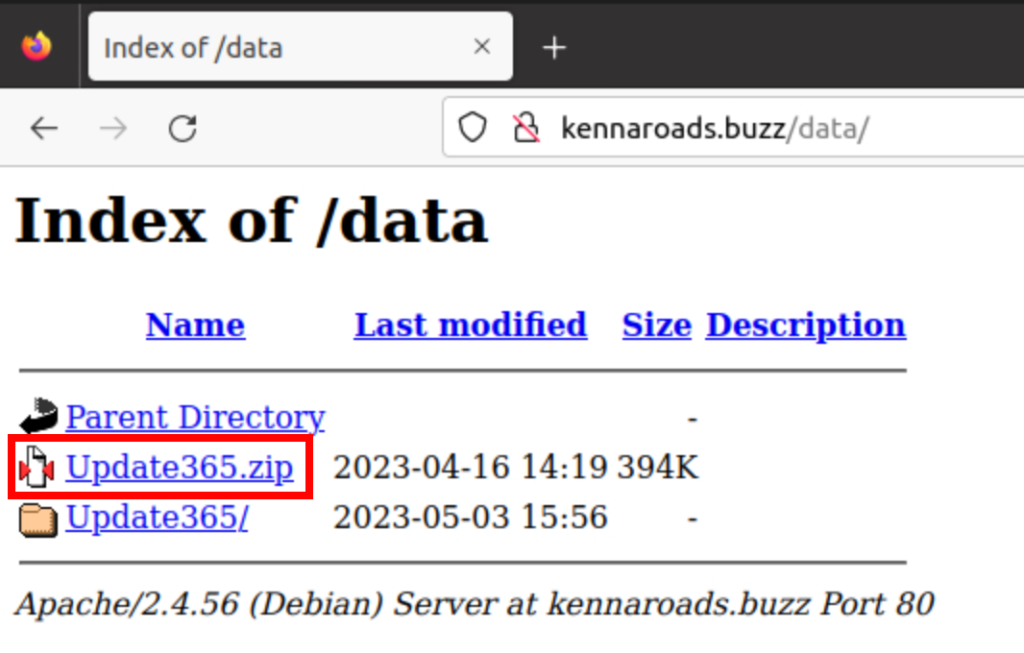
We’re going to download this and check its hash.
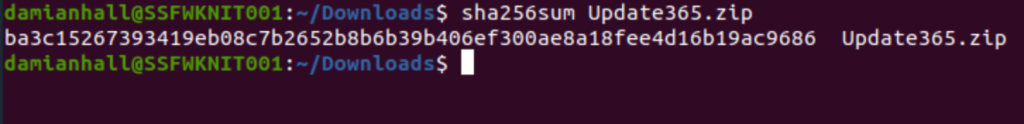
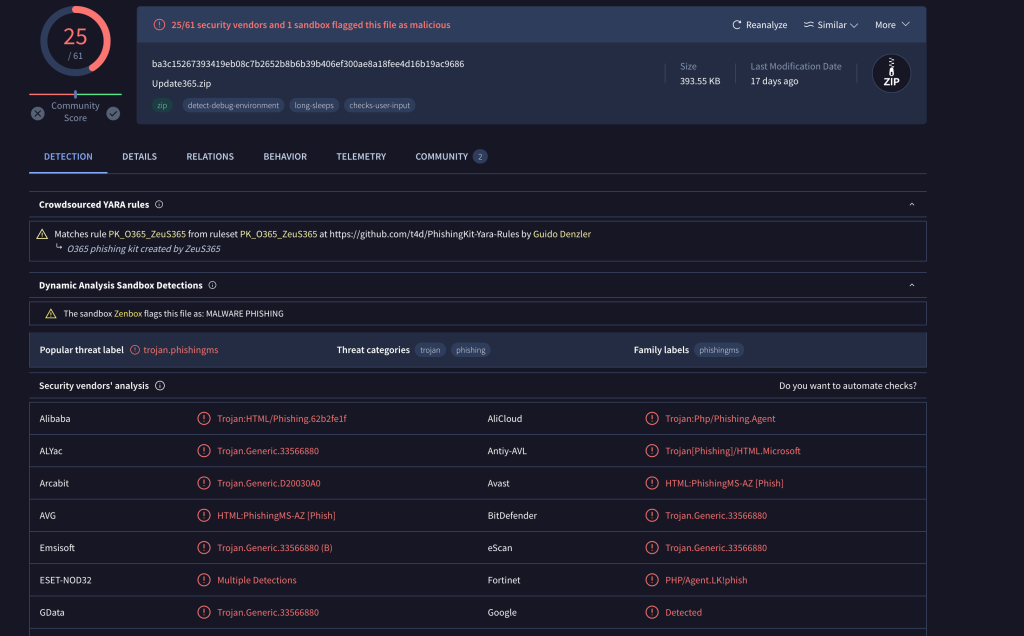
Now we have a hash value for the .zip file that would be downloaded if one of the targets fell for the attack putting this into virus total shows us that it is a Trojan and a part of a phishing kit
Email 2:
The next email we will be looking at is a part of the same targeted phishing campaign from the previous email we took a look at.
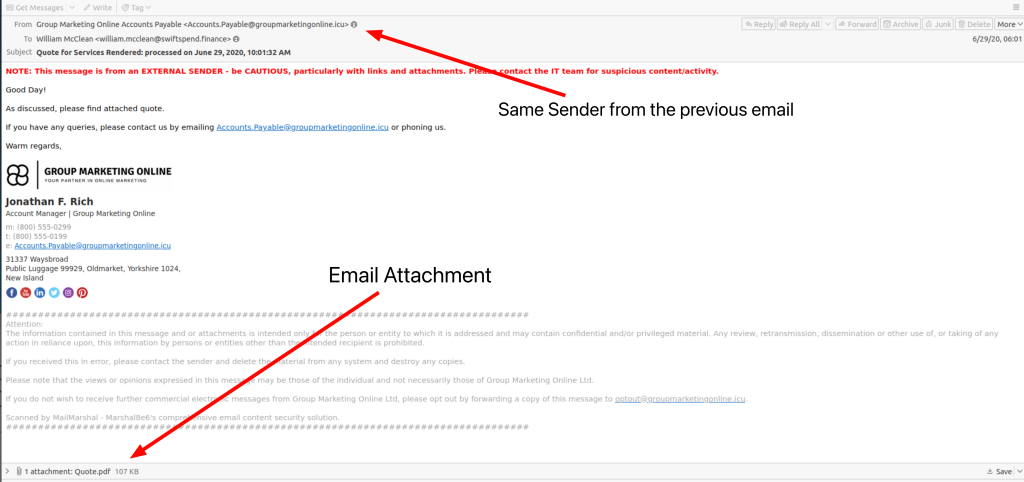
Opening up the attachment we get a PDF
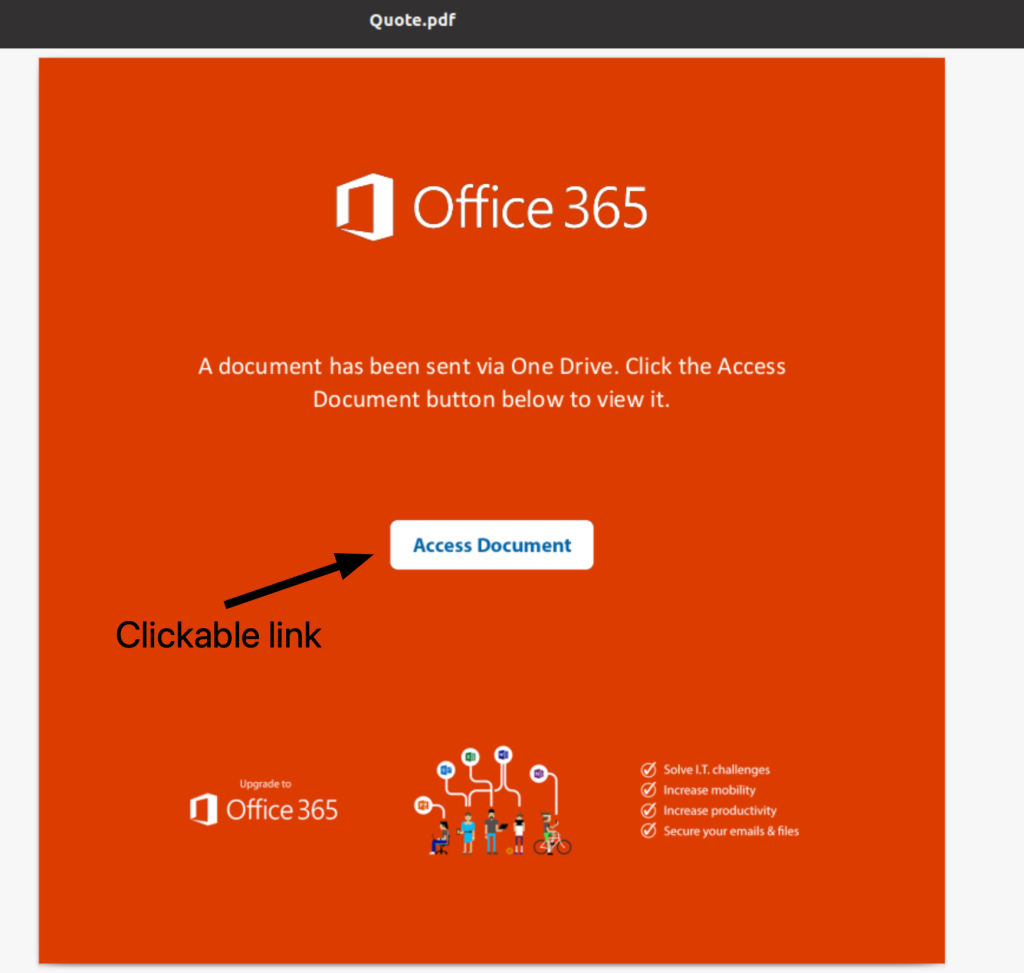
Clicking on the link embedded in our PDF telling us that the “quote” has been sent to us in one drive
Opening this link sends us to the same page as before but customized to the target of the email.
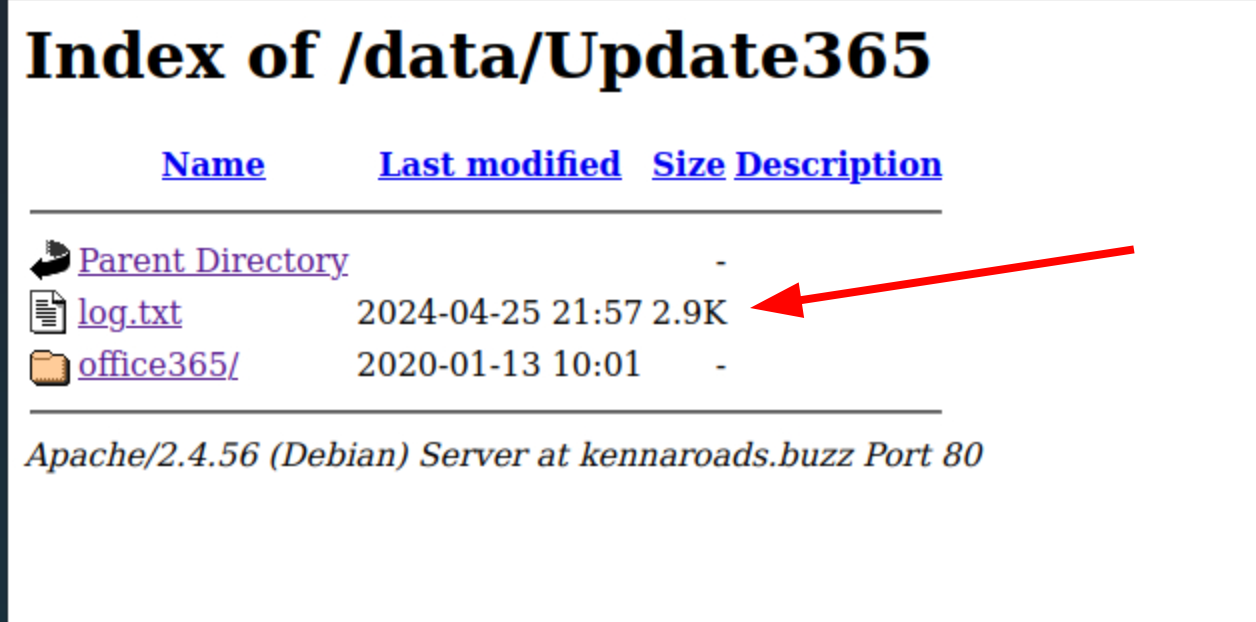
Taking a closer look at the directories on the site gives us a lot of information
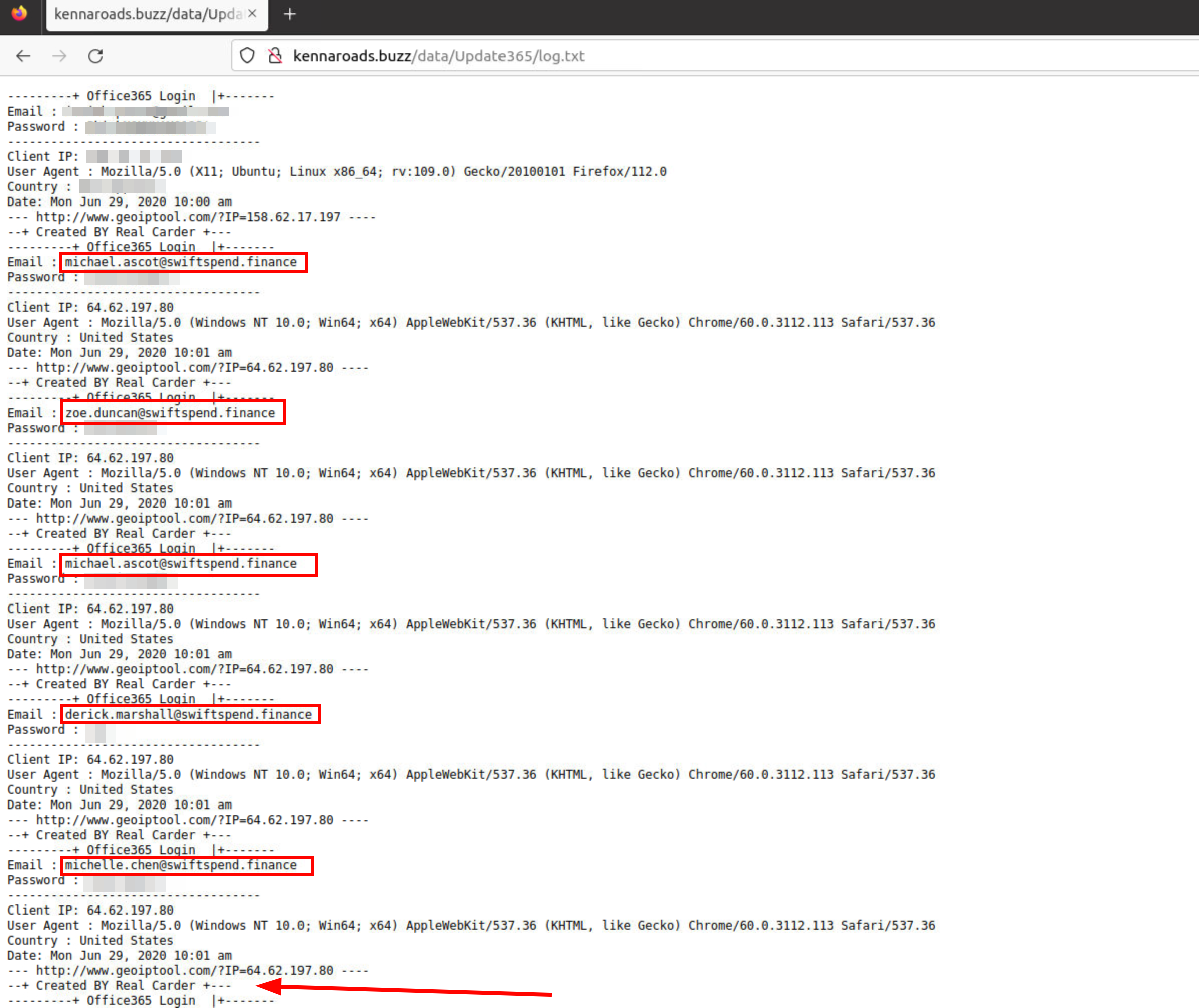
When looking through the site directories we found that we can see the log file of the phishing page and the emails and passwords of the users phished in clear text as well as the creator of the phishing page named “real carder”.
If this were a live incident and phishing campaign that were to happen on your network you would immediately want to start containment & remediation of effected machines, and changing user credentials. Having the effected users participate in a form of user awareness against phishing emails and common threats they may encounter is a great way to prevent it from happening again in the future.
we’ve dissected several phishing emails to understand their common tactics and red flags. By examining these examples, we’ve equipped ourselves with the knowledge to better spot deceitful attempts and protect our personal information from cyber threats. Now, let’s take this theoretical knowledge into the practical realm. Next I’ll dive into my spam folder to show you scam emails I’ve received. We’ll analyze them together to see how our newfound insights hold up in the wild.
Quick look into another example from my spam folder
Looking at some real life examples of spam/phishing from my inbox

One of the many phishing attempts caught in one of my email account’s spam folder. We can see a lot of the common tactics used when it comes to phishing / general scam attempts. There’s a sense of urgency I need to renew my subscription today in order to get 90 days worth of free service from Sirius XM
The email was also sent from an unfamiliar sender
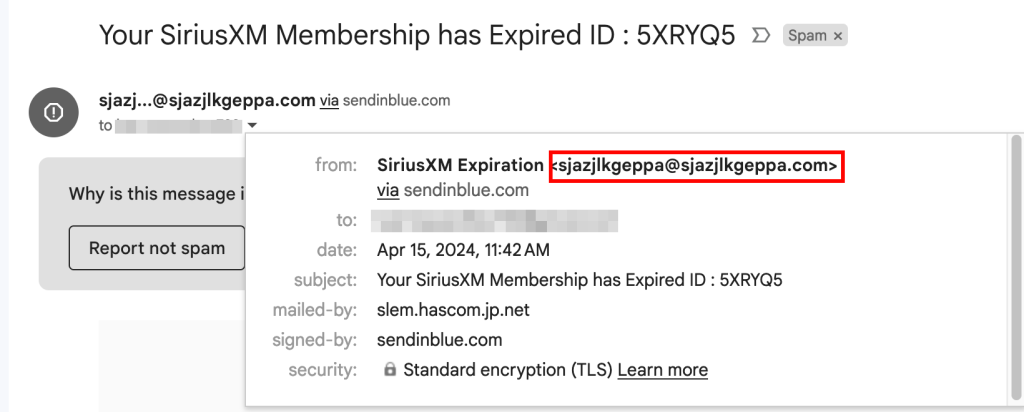
This is obviously not from Sirius XM, but they are attempting to spoof being Sirius XM (poorly) by using a display name that indicates it’s from Sirius XM
Opening the link inside a sandbox we are met with this
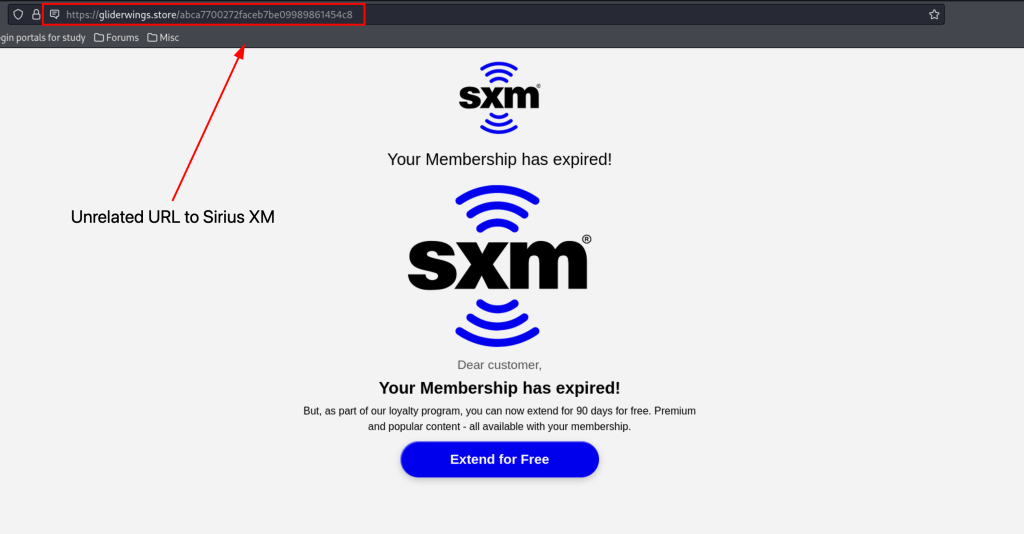
Immediately upon clicking the link we get multiple URL redirects and then are brought to this landing page when everything finishes redirecting us to the desired URL. The site does not use HTTPS and instead uses the insecure HTTP
HTTP does not encrypt the data being transmitted between the browser and the server. This means that any information sent over HTTP is in plain text and can be intercepted by others.
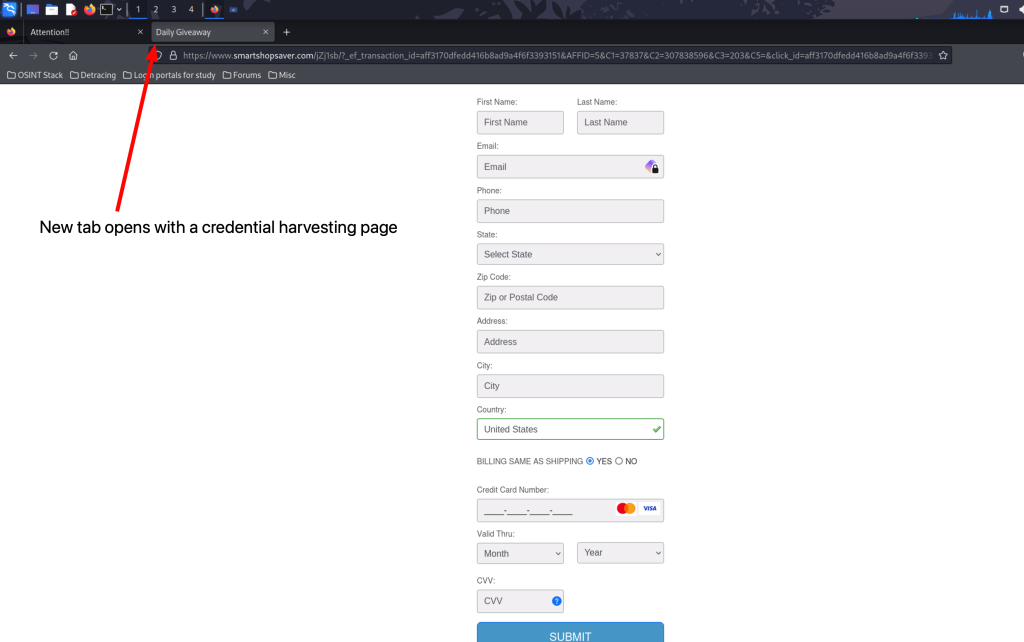
Moving forward by clicking “to extend our membership for free”
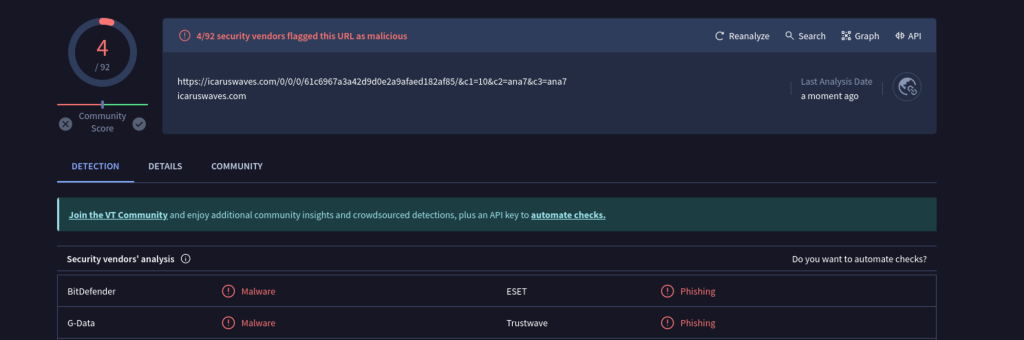
When plugging one of the redirect URL’s into virus total we can see that it has been flagged as a phishing site with malware
The First Line of Defense Against Phishing
While technological safeguards like spam filters and antivirus software play huge roles in protecting against phishing, the human element can’t be overlooked. User awareness and education are perhaps the most effective defenses an organization can have against these attacks.
Phishers often exploit a lack of awareness, hunting for users who might not recognize the subtleties of a phishing attempt or just like clicking on every blue link and attachment that comes in their inbox. Common tactics include creating a sense of urgency, impersonating authority figures, and leveraging current events or personal information to make attacks more convincing.
Educating employees about these tactics, and more importantly, training them to handle and report suspicious emails, can significantly strengthen an organization’s internal security.
A well-informed employee is the most effective deterrent to phishing.